Guidance on the Legacy IT Risk Assessment Framework
Updated 13 March 2025
Introduction
This guidance outlines the Legacy IT Risk Assessment Framework, a qualitative risk-based approach designed to evaluate the criticality of legacy-related risks across government entities. The framework has been developed in collaboration with departments. It utilises established legacy frameworks and industry models, this self-assessment tool is tailored for use by public sector organisations. All ministerial departments have been integrated into the framework.
The framework is a standard mechanism for the central government, Central Digital & Data Office (CDDO), to gauge the technical health of legacy IT assets, enabling strategic allocation of focus and funding for the wider legacy estate of the government. It assures that efforts towards remediation are concentrated on systems with the highest risk factors.
This document provides insight into the origins of the framework and gives comprehensive guidance to departments for accurate utilisation and interpretation of the risk assessment framework.
This guidance will help you to:
- Assess both the impact and likelihood of a specific legacy IT system
- Assess if that legacy IT system is considered ‘red-rated’
- Apply best practice for the management of legacy IT
This guidance will not:
- Provide details of specific solutions to treat legacy IT systems
What is legacy IT?
In the realm of technology, the term ‘legacy IT’ refers to the outdated and often obsolete technology systems, software, and hardware that have been in use for a considerable period of time. These systems might have been implemented years or even decades ago to support various functions within government organisations. However, due to technological advancements, changing requirements, and the rapid pace of digital transformation, these legacy IT systems have become less efficient, harder to maintain, and sometimes incompatible with modern security standards.
Legacy IT encompasses a range of technology components, including operating systems, databases, applications, and infrastructure, that may have been customised and integrated over time to suit specific departmental needs.
Although these systems might have served their purpose effectively when first implemented, they now present several challenges and risks to government departments. These challenges include higher maintenance costs, limited scalability, reduced agility, increased susceptibility to cyber threats, and difficulties in integrating with newer, more advanced systems.
Recognising the importance of modernisation and the need to keep pace with technological advancements, government departments are increasingly focused on addressing the issues posed by legacy IT. Initiatives are being undertaken to assess, prioritise, and upgrade or replace these outdated systems with more modern and efficient solutions. This transition not only enhances operational efficiency but also improves data security, user experience, and the ability to deliver public services effectively.
Indicators that a system is considered as legacy:
- Software out of Support
- Expired vendor contracts
- Too few people with required knowledge and skills
- Inability to meet current or future business needs
- Unsuitable hardware
- Known security vulnerabilities
- Recent problems/downtime
What is the Legacy IT Risk Assessment Framework?
Within the Transforming for a digital future: 2022 to 2025 roadmap for digital and data, published in June 2022, a commitment was agreed by the government. This commitment was to define and identify all ‘red-rated’ legacy systems through an agreed cross-government framework. It also committed that these systems will have agreed remediation plans in place.
This framework is a tool for identifying legacy IT assets and those which are classed as ‘red-rated’ systems.
The Legacy IT Risk Assessment Framework provides a structured approach for evaluating and prioritising the risks associated with outdated IT systems within government departments.
By systematically assessing the likelihood and impact of system issues, departments can make informed decisions to mitigate risks, enhance operational efficiency, and contribute to the broader goals of modernisation and digital transformation.
What does a ‘red-rated’ system mean?
A ‘red-rated’ system refers to an IT system that has been assessed and scored as having both high likelihood and high impact in terms of potential risks, and more specifically if a system has an overall risk score of 16 or above[1] . In the context of risk assessment frameworks, a ‘red-rated’ system is one that falls into the highest-risk category.
When a system is labelled as ‘red-rated’, it signifies that the system is at a critical level of risk, where the likelihood of encountering issues or failures is significant, and the potential impact of these issues could be severe. Essentially, it’s an alert that draws attention to systems that require immediate attention, mitigation, or remediation due to their potential to cause substantial harm, disruption, or negative consequences if left unaddressed.
In the context of legacy IT systems, ‘red-rated’ systems likely exhibit a combination of factors that make them more vulnerable, such as outdated technology, lack of support, susceptibility to security breaches, and potential hindrance to meeting business needs. Therefore, these systems should be given top priority for management, modernisation, or replacement to reduce their risk and ensure the continued smooth operation of the organisation’s IT infrastructure.
What government organisations does this framework apply to?
Currently all ministerial departments have been onboarded to the framework, as they have been mandated to provide their assessments by end of the financial year 2023/24’.
Although not mandated to all Public sector organisations, having a consistent and structured approach to managing Legacy IT will help Public sector organisations understand how their risks compare to other organisations, identify commonalities across departments and support shared solutions on technology and suppliers
Legacy IT Risk Assessment Framework overview
The Legacy IT Risk Assessment Framework utilises two categories of criteria: Likelihood and Impact.
Each category is further divided into specific criteria to provide a comprehensive assessment of risk levels. The assessment is conducted over an assumed 3-year period.
Likelihood Criteria
These criteria cover seven different dimensions of Likelihood, allowing for an assessment of the chance of system issues e.g. failure being realised.
How to effectively apply the criteria:
L1 End of Life / End of Support
- Level to which the technology used is out of support, i.e. technical support, upgrades, patches, and new features
L2 Expired Vendor Contract
- Level to which support contracts for services are due to expire with no replacement agreement
L3 Lack of Knowledge and Skills
- Prevalence of personnel with skills and knowledge to provide support and make changes to the asset
L4 Inability to Meet Current or Future Business Needs
- Technical inability for asset to meet current or future business needs (e.g. inability to be scaled or have improvements applied)
L5 Unsuitable Physical Environment
- Degree to which the asset is based on old hardware or housed in improper physical environment (e.g. due to climate, location)
L6 Known Security Vulnerabilities
- Likelihood that security vulnerabilities exist
L7 Historically Recorded Issues
- Evidence of historical failures or issues
Impact Criteria
These criteria cover six different dimensions of Impact. Impact resulting directly or indirectly from system issues e.g. failure or attack
How to effectively apply the criteria:
C1 National Security Impact
- Impact of a failure of the system directly or indirectly resulting in a threat to national security, health, personal safety or loss of human life
C2 Reputational Impact
- Impact to perception of UK Government and scale of intervention to manage damage to reputation
C3 Direct Financial impact
- Financial impact, either absolute or percentage of departmental budget, that would result from regulatory, litigation, citizen redress or other direct costs including exist-costs and break-clauses
C4 Direct External Stakeholder Impact
- Impact on external stakeholders, including economic loss and/or significant inconvenience
C5 Operational Impact
- Extent of resource hours lost or additional workload hours required following outage
C6 Impact on other Systems (Technical Barrier to Innovation)
- Level of difficulty in improving the system due to significant codependency on other systems
Scoring Mechanism
The following scores are used to assess against each criterion for both likelihood and impact tables:
Likelihood
6. Certain
5. Very High
4. High
3. Medium
2. Low
1. Very Low
Impact
5. Very High
4. High
3. Medium
2. Low
1. Very Low
Considering an IT asset as Legacy
Legacy assets are those which score a 3 (medium-level) or higher in any of the legacy likelihood criteria.
Considering an IT asset as Legacy - ‘red-rated’
If a system has an overall risk score of 16 or above, normally from a High or above in any criteria for the likelihood and impact tables, it would be classed as a ‘red-rated’ system and must be updated on the Central Digital & Data Office (CDDO) Legacy IT Asset Register.
The highest possible overall risk score is 30.
Legacy IT Risk Assessment Framework
Likelihood
Likelihood - Propensity of system issues e.g. failure being realised
| Level | Degree | L1 End of Life / End of Support | L2 Expired Vendor Contract | L3 Lack of Knowledge and Skills | L4 Inability to Meet Current or Future Business Needs | L5 Unsuitable Physical Environment | L6 Known Security Vulnerabilities | L7 Historically Recorded Issues |
|---|---|---|---|---|---|---|---|---|
| 6 | Certain | Already out of support | Already out of vendor contract | Already insufficient expertise | Already not meeting current business needs | Hardware or physical environment is currently unsuitable | Security vulnerabilities known to currently exist | Issues or failures are currently occurring |
| 5 | Very High | Very high likelihood technology will be out of support | Very high likelihood vendor contracts will expire with no replacement agreement in place | Very high likelihood that expertise to provide support or make changes to the asset will become an issue | Very high likelihood that the system will be unable to meet its business needs | Very high likelihood level of concern regarding the suitability of the hardware or physical environment | Very high likelihood that security vulnerabilities exist | Severe issues or failures have occurred in recent past |
| 4 | High | High likelihood technology will be out of support | High likelihood vendor contracts will expire with no replacement agreement in place | High likelihood that expertise to provide support or make changes to the asset will become an issue | High likelihood that the system will be unable to meet its business needs | High level of concern regarding the suitability of the hardware or physical environment | High likelihood that security vulnerabilities exist | Major issues or failures have occurred in recent past |
| 3 | Medium | Medium likelihood technology will be out of support | Medium likelihood vendor contracts will expire with no replacement agreement in place | Medium likelihood that expertise to provide support or make changes to the asset will become an issue | Medium likelihood that the system will be unable to meet its business needs | Medium level of concern regarding the suitability of the hardware or physical environment | Medium likelihood that security vulnerabilities exist | Moderate issues or failures have occurred in recent past |
| 2 | Low | Low likelihood technology will be out of support | Low likelihood vendor contracts will expire with no replacement agreement in place | Low likelihood that expertise to provide support or make changes to the asset will become an issue | Low likelihood that the system will be unable to meet its business needs | Low level of concern regarding the suitability of the hardware or physical environment | Low likelihood that security vulnerabilities exist | Minor issues or failures known to have occurred in recent past |
| 1 | Very Low | Very low likelihood technology will be out of support | Very low likelihood vendor contracts will expire with no replacement agreement in place | Very low likelihood that expertise to provide support or make changes to the asset will become an issue | Very low likelihood that the system will be unable to meet its business needs | Very low likelihood level of concern regarding the suitability of the hardware or physical environment | Very low likelihood that security vulnerabilities exist | No issues or failures known to have occurred in recent past |
Impact
Impact resulting directly or indirectly from system issues e.g. failure or attack
| Level | Degree | C1 National Security Impact | C2 Reputational Impact | C3 Direct Financial impact | C4 Direct External Stakeholder Impact | C5 Operational Impact | C6 Impact on other Systems (Technical Barrier to Innovation) |
|---|---|---|---|---|---|---|---|
| 5 | Very high | Very high sustained impact, including threats to health, personal safety or loss of human life | Very high impact to perception of UK government, requiring major intervention at a parliamentary level to manage reputation | Very high impact e.g. >10% or >£50m of impact, related to regulatory, litigation, citizen redress, and other direct costs | Very high impact on external stakeholders, including economic loss and/or significant inconvenience | Very high impact e.g. >500,000 resource hours of idleness or increased workload | Very high barrier to innovation, e.g. highly integrated with other systems, significantly increasing build cost or duration for other projects |
| 4 | High | High impact to national security, health, personal safety or loss of human life | High impact on perception of UK government, requiring significant intervention to manage reputation | High impact e.g. 8-10% or £21-50m of financial impact, related to regulatory, litigation, citizen redress, and other direct costs | High impact on external stakeholders, including economic loss and/or significant inconvenience | High impact e.g. 100,001-500,000 resource hours of idleness or increased workload | High barrier to innovation |
| 3 | Medium | Medium impact to national security, health, personal safety or loss of human life | Medium impact on perception of UK government, requiring some intervention to manage reputation | Medium impact e.g. 5-7% or £11-20m of financial impact, related to regulatory, litigation, citizen redress, and other direct costs | Medium impact on external stakeholders, including economic loss and/or significant inconvenience | Medium impact e.g. 1001-100,000 resource hours of idleness or increased workload | Medium barrier to innovation, e.g. integrated with some systems, sometimes increasing build cost or duration for projects |
| 2 | Low | Low impact to national security, health or personal safety | Low impact on perception of UK government, requiring little intervention to manage reputation | Low impact e.g. 1-4% or £5-10m of financial impact, related to regulatory, litigation, citizen redress, and other direct costs | Low impact on external stakeholders, including economic loss and/or significant inconvenience | Low impact e.g. 101-1000 resource hours of idleness or increased workload | Low barrier to innovation |
| 1 | Very low | Very low impact to national security, including threats to health or personal safety | Very low impact on perception of UK government, requiring no intervention to manage reputation | Very low impact e.g. <1% of departmental budget or <£5m of financial impact related to regulatory, litigation, citizen redress, and other direct costs | Very low impact on external stakeholders, including economic loss and/or significant inconvenience | Very low impact e.g. <100 resource hours of idleness or increased workload | Very low barrier to innovation, e.g. no interactions with other systems |
How to use the risk assessment framework
To effectively utilise the assessment framework, follow these steps:
- Identification: Begin by identifying the specific IT system under consideration and its associated components, including hardware, software, and support contracts.
- Likelihood Assessment: Evaluate each of the Likelihood criteria (L1-L7) for the system in question. Assign a level of likelihood (e.g. Low, Medium, High etc) based on available information and expert judgement. This assessment should reflect the probability of each criterion occurring over the assumed 3-year period.
- Impact Assessment: For each Impact criterion (C1-C6), analyse the potential consequences of a system failure or issue. Assign an impact level (e.g. Low, Medium, High etc) based on the severity and scope of the consequences.
- Aggregate likelihood and impact scores: The overall scores from both likelihood and impact criteria are aggregated. This is done by finding the average of the mean of the scores and the maximum score, resulting in an overall risk score.
- Risk Categorisation: If a system is assessed and scored with an overall risk score of 16 or above, it is then considered ‘red-rated’. This indicates a nationally critical level of risk requiring immediate attention.
- Prioritisation and Action: Systems with a ‘red-rated’ status represent the highest level of risk due to their combination of high likelihood and high impact. These systems should be prioritised for urgent modernisation, updates, or replacement. Lower-risk systems can be addressed in subsequent phases. Note that the assigned Likelihood and Impact levels can be plotted on a risk matrix to help visualise the relative risk levels for different systems within your estate.
- Regular Review: Perform periodic reviews of the Legacy IT systems to account for changes in technology, business needs, and security threats. Adjust the Likelihood and Impact assessments accordingly.
- Submit Assessment to CDDO: All Ministerial departments are mandated to provide all their assessments to the central CDDO Legacy IT Asset Register. These assessments must be updated annually to ensure accurate data is used for reporting and monitoring. Other non-ministerial departments, agencies and organisations are also encouraged to provide their assessments, as this creates a richer picture of legacy IT across the wider government.
Example scoring of a legacy IT asset
This is a fictional asset that has been assessed using the framework. Each of the total likelihood and impact scores can be used to plot on a 2-axis risk matrix. The result is an overall risk score which can be used to measure against other assets in the department or across government.
Department: ‘Ministry of Space Transport Infrastructure’
Asset Name: ‘HR Management Plus’
Likelihood criteria scores (criteria L1-L7, score 1-6): L1= 5 (i.e. Very High), L2= 5, L3= 5, L4= 5, L5= 6, L6= 6, L7= 6
Likelihood mean score: 5.43
Likelihood max score: 6
Total likelihood score (avg between mean and max): 5.71
Impact criteria scores (criteria C1-C6, score 1-5): C1= 5 (i.e. Very High), C2= 5, C3= 2, C4= 5, C5= 5, C6= 4
Impact mean score: 4.33
Impact max score: 5
Total impact score (avg between mean and max): 4.67
Overall Likelihood x Impact risk score (5.71 x 4.67) : 26.67
Following the assessment by a subject matter expert in the department, this asset has scored over 16, it is therefore considered a ‘red-rated’ legacy IT asset. The assessment results will now be submitted to CDDO Legacy IT Asset Register.
Providing a cross government view of legacy IT risk
Using the same framework across government allows for the identification of commonalities across Public sector organisations such as red-rated systems - i.e. those that are the most likely to fail and have the greatest impact of failure.
The Central Digital and Data Office (CDDO) uses the data gathered from department assessments of their legacy IT to create a central picture of where the highest risks are.
This example 2-axis risk chart shows a number of legacy IT assets plotted against both likelihood and impact, coloured to indicate the department they belong to.
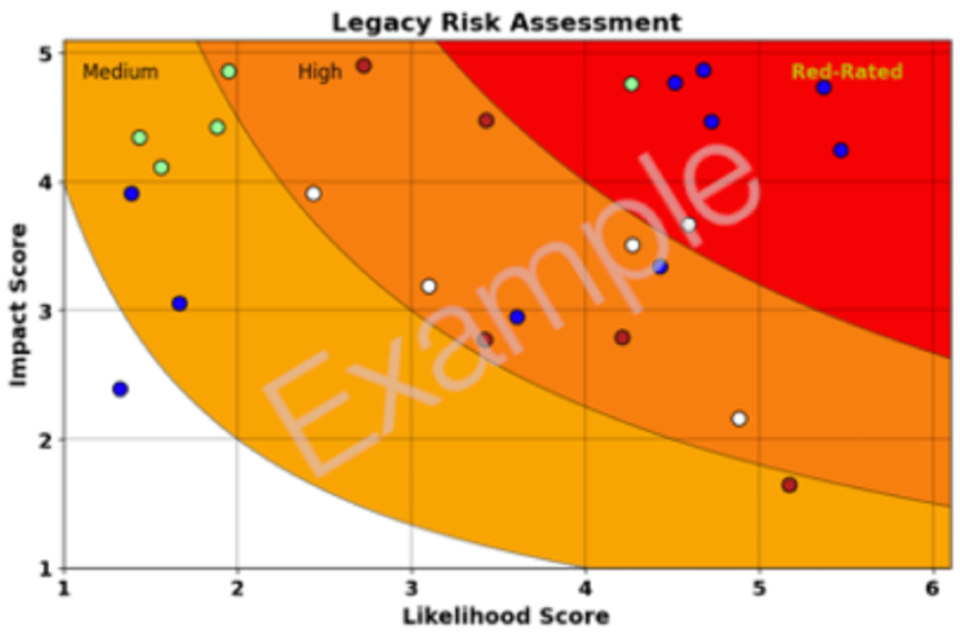
CDDO Legacy IT Asset Register
All Ministerial departments are mandated to provide all their legacy IT assessments to the Central Digital and Data Office (CDDO) each year. This is to ensure that the government has an accurate overview of all ‘red-rated’ assets. This overview is used to provide visibility to ministerial committees and senior civil service boards on the state of legacy IT in government.
Although the priority is to identify those IT systems that are ‘red-rated’ the process also allows for the capture of other legacy IT systems.
Whilst this central register holds the details on the risk scoring, it also expands the details regarding the legacy IT system. It captures details on:
- The remediation approach, i.e. Does a mitigation plan exist? Is this plan funded? What is the target resolution data? Any further remediation milestones
- A description of the IT asset, i.e. What type of system is it? What does it do, its purpose? What are the legacy components?
- Services, i.e. What services or business capabilities does the asset support?
- Finances, i.e. What is the estimated % reduction (or increase) in annual running costs if this asset were no longer legacy?
- Assessment metadata, i.e. The date the asset was assessed and who assessed it
Best practice for treating a legacy IT system
This content provides general guidance and should be adapted to align with the specific needs and requirements of individual government departments.
Legacy IT systems, due to their outdated technology and inherent complexities, can pose significant challenges and vulnerabilities to an organisation’s IT landscape. In the context of UK government departments, these systems often demand special attention and care. The following points outline a strategic approach to treating and managing legacy IT systems, emphasising their potential vulnerabilities compared to modern counterparts.
Assessment and Prioritisation
- Begin by conducting a thorough assessment of all legacy IT systems within the department
- Utilise the Legacy IT Risk Assessment Framework to categorise systems based on their likelihood and impact levels
- Systems rated as ‘red-rated’ due to high likelihood and high impact should be prioritised for immediate action
Modernisation and Migration
- Consider modernising and migrating critical legacy systems to current cloud technologies and platforms. This might involve re-architecting, rewriting, or replacing components
- Modern systems often benefit from improved security, compatibility, and maintainability
Security Enhancement
- Legacy systems are often more vulnerable to cyber threats due to outdated security protocols and lack of regular updates
- Implement robust security measures such as firewall protection, intrusion detection systems, and regular vulnerability assessments
- Additionally, segregate legacy systems from critical data to minimise potential breaches
Isolation and Segmentation
- Isolate legacy systems from the rest of the network, creating segments that minimise the attack surface
- Limit communication pathways and enforce strict access controls
- This containment strategy helps prevent potential threats from propagating to other parts of the network
Regular Patching and Updates
- Establish a routine schedule for applying patches, updates, and security fixes to legacy systems
- While it might be challenging to find patches for outdated software, dedicated effort is necessary to minimise known vulnerabilities
Backup and Disaster Recovery
- Implement comprehensive backup and disaster recovery plans for legacy systems
- These systems might be more prone to failures, making a robust recovery strategy essential to minimise downtime and data loss
Legacy Code Review and Documentation
- Regularly review and document legacy code to understand its intricacies and dependencies
- Maintain a knowledge repository to ensure that critical operational knowledge isn’t lost due to staff turnover
Staff Training and Skill Enhancement
- Invest in training and upskilling your IT staff to manage legacy systems effectively
- Encourage the development of skills that are specifically relevant to the maintenance and security of older technologies
Vendor Support and End-of-Life Management
- If vendor support for legacy systems is still available, engage with vendors to ensure you receive essential security updates and patches
- If vendor support has ceased, consider collaborating with third-party experts who specialise in legacy system management
Monitoring and Incident Response
- Implement comprehensive monitoring tools to detect any suspicious activity within legacy systems
- Develop incident response plans specific to these systems to minimise the impact of breaches or failures
Treating and managing legacy IT systems requires a proactive and strategic approach. Due to their inherent vulnerabilities, these systems demand careful attention to ensure security, reliability, and compliance with evolving regulations.
By following these best practices, government departments can effectively address the challenges associated with legacy IT systems while safeguarding their critical operations and data.
Contact
Who to contact for further information
GDS Team
technology.management@digital.cabinet-office.gov.uk
You can email for assistance with:
- Implementing the Legacy IT Risk Assessment Framework
- Support with using the criteria to assess a legacy IT system
- Feedback on the framework
