Managing information risk
A guide to assessing and making business decisions about technology and information risks.
This is an ALPHA release and we welcome feedback to help us shape further releases. Please send any feedback to enquiries@cesg.gsi.gov.uk.
Introduction to risk management
What is risk?
What a risk is, and how it’s described, depends entirely on the context of the organisation which faces that risk, and on the biases of the individual assessing it.
In the context of wider business risk management, a risk is the potential for either harmful or positive outcomes to impact upon business objectives, including reputation. Organisations cannot develop without taking risks. Technology and information risk is not just about avoidance and mitigation; the pursuit and acceptance of risk creates opportunities and can help deliver business objectives.
Having recognised this wider meaning, this guidance uses the word ‘risk’ to describe the potential for security harm to occur as a result of using technology and information to achieve business objectives.
It is important not to just think about risk in the context of the confidentiality, integrity and availability of technology and information. In addition to these, other things that the organisation cares about (eg its reputation) may be at risk and should also be taken into account.
What is risk management?
Risk management describes the decisions an organisation makes and the actions it takes in response to risks that have been identified.
The purpose of risk management is to help the organisation protect itself, and provide it with confidence that the technology and information it uses is secure enough to meet its needs.
Where risk management decisions and actions affect multiple organisations (or multiple parts of an organisation) in an enterprise context, then some level of risk management co-ordination is likely to be required.
Since all of the following change over time:
- the needs of the organisation
- the threats it faces
- the vulnerability of technology and information
Risk management needs to happen throughout the lifecycle of a system or service, informed by a realistic view of risk and a clear understanding of the organisation and its objectives.
Technology and information risk is just one area of business risk that organisations need to manage. As such it should fit in with the existing business risk management activities undertaken by an organisation.
What is risk assessment?
Risk assessment is a key risk management activity that identifies, assesses and articulates risks to the organisation. Risk assessment is needed to inform risk management decision making, and it requires technical, security and business skills and knowledge.
Organisations may use different risk assessment methods to assess the risks associated with particular areas of their business (eg financial, legal, health and safety, etc). The choice of risk assessment method rests with the organisation and these choices are often based on the type of risk or business area under consideration. Achieving a consistent approach to describing and presenting risks from different areas of the organisation will help it to consume assessment output, and make informed risk management decisions.
Who makes risk management decisions?
The decisions made to manage technology and information risk are the responsibility of the organisation. They are not the sole responsibility of security or IT departments. Risk management decisions should be objective and informed by an understanding of risk. They should not be made in isolation but on a basis of understanding how individual decisions affect the wider business, and what it is trying to achieve.
Organisations should decide for themselves what risk management decisions need to be made to support the delivery and operation of a system or service, and could include:
- the authorisation of expenditure to design a system or service
- the authorisation of expenditure to build, test, install, run decommission a system or service
- the approval to use information, a system or a service during the test, install, run, and decommission stages of a system or service lifecycle
The right people need to make decisions at the right time, with the right advice and support. They need to be empowered by the organisation and have the right business, technology, security knowledge and skills to enable informed and objective decisions.
Security Policy Framework and accreditation
Prior to April 2014, a security process called accreditation was mandated by the HMG Security Policy Framework (SPF), for all Government departments processing classified information. The process of accreditation provided for the assessment of a system against its security requirements, and approval was required from an accreditor as a prerequisite for operation. This was removed as a mandatory requirement from the April 2014 version of the SPF.
In some cases, the process of accreditation has lead to technology decisions being made outside the wider business decision making process, and treated as single delivery milestone, frequently left until the end of a project. The term accreditation has also been misused to describe the security status of a system or service (for example, “it is accredited” or “it must be accreditable”), an approach that can encourage a binary yes/no response to decision making when a more agile approach is required.
When accreditation is done well it takes account of what the organisation is trying to achieve and provides confidence that technology and information is secure enough to meet business needs.
It is not necessary for all organisations to establish an accreditation process, or appoint a dedicated accreditor, because there is no single risk management process or governance structure that fits all scenarios. This does not mean there is no need to manage risks or make informed and objective decisions; organisations should establish the processes and approaches that are right for them, and applying this guidance will help to achieve this.
Government organisations should note that a number of business roles are mandated by the SPF for good governance. Experience has shown that some of the best decision making approaches are those where it is clear who owns the risk, and who has the difficult challenge of balancing the business imperative versus any remaining risk.
It is important to recognise that as long as the system or service is in operation, then the organisation is, in reality, accepting the risks (whatever those might be). Stating that a system is “unaccreditable” or “not accredited” whilst it is still allowed to operate is meaningless.
Using technology to deliver business benefit attracts risk. Applying the principles described below will help organisations to understand how to approach the assessment and management of risks.
Technology and information risk management at a glance
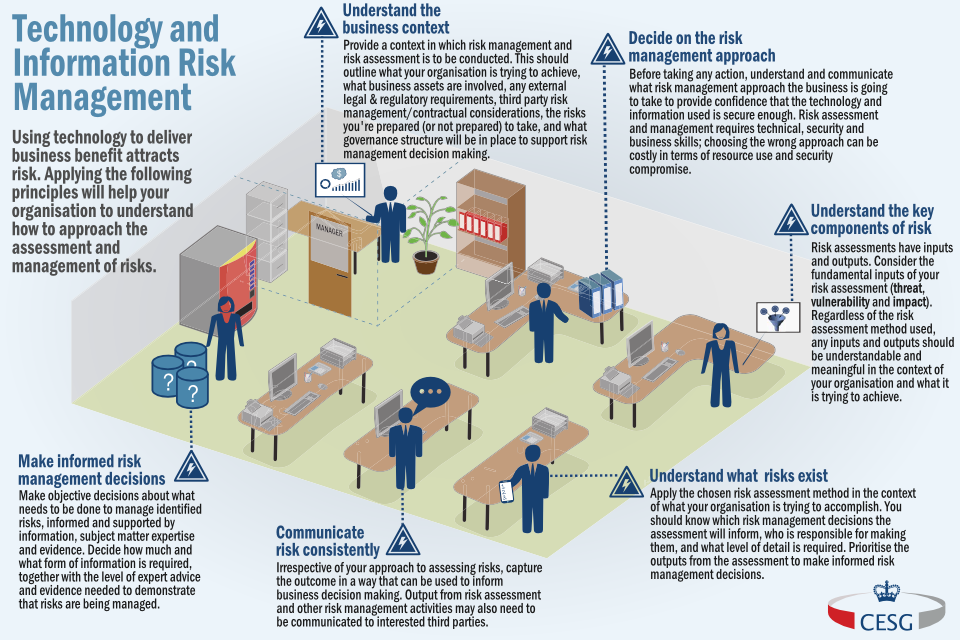
Technology and information risk management at a glance
Download a PDF version of this infographic here:
Understand the business context
Taking risks is a necessary part of doing business in order to create opportunities and help deliver business objectives. Organisations should always be aware of the risks they are taking to achieve their aims.
To ensure meaningful outcomes, organisations need to provide a context in which risk management and risk assessment is conducted. This context can be set by answering the following questions:
- what is the organisation trying to achieve, and what does it really care about?
- what business assets are involved (for example systems, services, information and other business assets such as reputation), and what are they worth to the organisation?
- what risks is the organisation prepared/not prepared to take with those assets to achieve its objectives?
- are there any external legal and regulatory requirements that need to be considered?
- are there any third party risk management or contractual considerations to take into account?
- what rewards may be realised by taking risks?
- what governance structure will the organisation have in place to support risk management decision making?
Those responsible for making risk management decisions should contribute to, and agree with, the formulation of this context.
Decide on the risk management approach
Before taking any action, the organisation must understand and communicate what risk management approach the business is going to take to provide confidence that the technology and information used is secure enough. This is an important business decision because the security of the organisation and its assets depend on it.
Risk assessment and other risk management activities require technical, security and business skills and knowledge and resources. Choosing the wrong approach could be costly in terms of resource use and security compromise.
Three potential risk management approaches are briefly outlined below:
Rely on the security provided by commercial products and services
In this approach, the organisation relies on the security provided by a commercial product or service, without conducting further security analysis. If the organisation adopts this approach, then there is no need to conduct customised technology and information risk assessments to help specify additional security controls. However, the organisation must accept that:
- it is completely reliant on the security claimed to be provided by commercial products and services, which can vary from ‘very robust’ to ‘almost none at all’
- security won’t be tailored to any specific needs the organisation might have
From a security perspective, this approach does not mean ‘do nothing’. Organisations that choose to take this approach still need to:
- have in place organisational controls (for example personnel security, physical security and security training for users)
- seek confidence and assurance that the commercial products and services they use are appropriate in the context of what they are doing and the threats they face
- make best use of the security provided natively by commercial products and services
Adopting this approach is dependent on having effective and appropriate commercial contracts and agreements in place. It should not be assumed that suppliers’ own standard commercial terms of business will provide an adequate basis for relying on the security provided by any product or service.
Organisations should also note that without risk assessment, the business will have no understanding of the technical and information risks it faces. This could result in a lack of security where it is needed, or the application of security where it is not needed, resulting in security compromise or unnecessary costs.
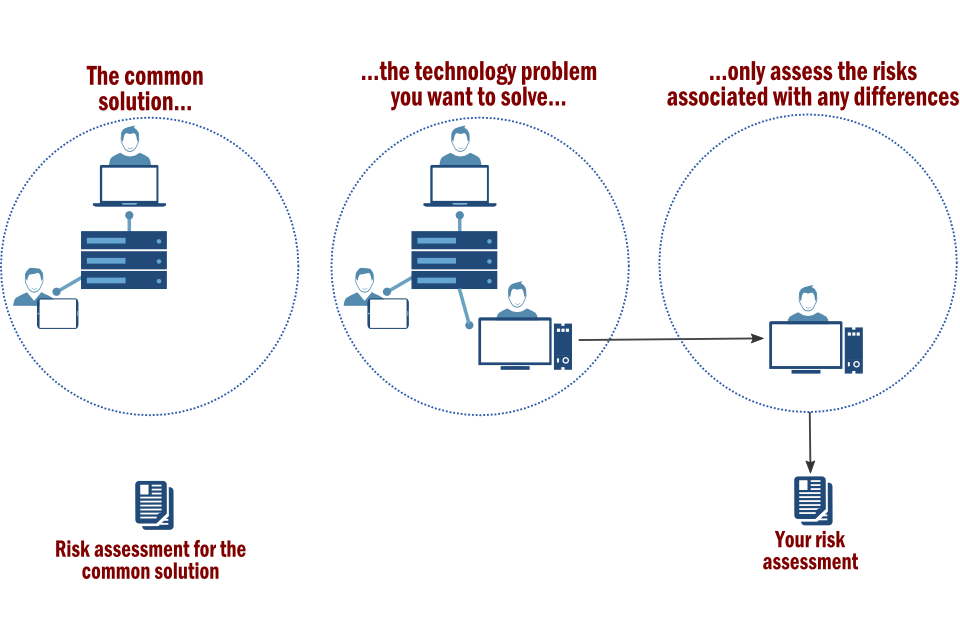
Apply common solutions to solve common problems
In this approach, the organisation applies the security provided by common security solutions to solve common technology problems. It only carries out tailored risk assessments (or specifies additional security controls) for those business objectives that are not entirely covered by the common solution.
This is illustrated in the diagram below:
Some examples of common solutions to common problems include:
- platform guidance
- BYOD guidance
- browser security guidance
- cloud security principles
- solutions provided by Digital Market place
- PSN
If the organisation decides that its business objectives are not entirely covered by the risk assessment for a common solution, the next step is to understand where the differences lie. For example, is there a unique threat or unique asset to be considered? Once these differences have been understood, then this can be used to form the basis of a more tailored risk assessment activity to specify additional security controls.
Carry out risk assessments to specify security controls
In this approach, the organisation chooses an appropriate risk assessment method and makes informed risk management decisions about what security controls it will implement. When making these decisions, the business may choose to:
- manage risks using controls that are independent of any predefined control set
- use security controls and control sets intended to implement local, national or international policies and standards (eg ISO/IEC 27001), these control sets are general in nature and need to be tailored to meet the needs of the organisation
Decisions will be informed by what the organisation is, and what it is trying to achieve. Some organisations in certain sectors may need to demonstrate that they have applied security controls to comply with standards or a sector-specific regulatory requirement. For example:
- external factors (eg legislation)
- organisations may need to apply security controls based on the type of information they need to protect (for example those that store and process personal data will need to apply controls to demonstrate compliance with the Data Protection Act (DPA))
- organisations seeking compliance with ISO/IEC 27001 may choose to apply its control set in the context of what it’s doing
- organisations conducting payment card transactions must apply the security controls and requirements set out in the Payment Card Industry (PCI) Data Security Standard
- certain business communities sharing services and infrastructure may choose to develop their own minimum set of security controls against which compliance can be demonstrated to protect the wider community
- organisations may choose to implement the advice provided by the 10 Steps to Cyber Security and/or the control set provided by the Cyber Essentials Scheme
- organisations making use of the PSN will need to demonstrate compliance against a prerequisite set of security controls as defined in the conditions for joining the network
The examples above should not be viewed as an exhaustive list of recommended control sets, as there are many to choose from. Some organisations may need to use a combination of control sets. Irrespective of the method, standard or framework used to make security control choices, decisions must be informed by and traceable to realistic risks affecting something that the organisation is actually doing.
Choose the right risk assessment method
There are many methods for conducting risk assessments, and numerous tools to support them. Most risk assessment methods can be aligned to the approaches described in the ISO 31000 and ISO 27000 series of International Standards which seek to identify, analyse and evaluate risks. The method to be adopted should be appropriate for the organisation, so this is ultimately a business decision. It should be scaled to support whatever delivery model is being used and for the target audience.
When choosing a risk assessment method, the organisation is likely to need to answer the following questions:
- can I define the inputs I need (threats, vulnerabilities and impacts) using a particular method?
- will the output from the method reflect meaningful risks in a way the organisation will understand?
- will the output allow me to understand and prioritise risks in a meaningful way?
- can the output be communicated to third parties?
- is the method of assessment proportionate to what it is I am trying to achieve?
- will I need to employ specialist resources to use it, or to interpret the output for the organisation?
- are there any costs associated with using the method?
- can I repeat the method or approach consistently?
- are there any contractual or commercial restrictions on how I can use the method?
- will the method support the commercial model operated by my organisation?
A discussion of popular methods in use today is provided in the final section of this guidance, and can be used as a starting point for answering these questions.
Understand the key components of risk
Risk assessments have inputs and outputs. The fundamental inputs to be considered in a risk assessment are threat, vulnerability and impact. Risk is normally realised as a consequence of these inputs, although some risk assessment approaches will include other inputs (such as likelihood and asset value). Regardless of the risk assessment method used, any inputs and outputs should be understandable and meaningful in the context of the business and what it is trying to achieve.
Threat
Threat describes the source of a risk being realised. Threats to systems and services include people who would seek to do the business harm through technology, and hazards such as environmental disasters and accidents. Some of the threats that an organisation may face are beyond the organisation’s control; they can only use threat-related knowledge to aid risk prioritisation.
- where appropriate to their organisation’s context, the business should apply the threat profile for OFFICIAL, supplemented if necessary with local or specific threat intelligence where it is available. It is not necessary to consider all threats in all scenarios. Further information on the threat profile for OFFICIAL is provided by the Government Security Classifications April 2014
- where threats are people, organisations should consider the motives that drive individuals to launch an attack, as well as their opportunities and capabilities to do so
- modelling threats can be a useful way of helping to understand what threats should be considered and how they may affect individual assets, the organisation and what it is doing
- to achieve consistency between different risk assessments within the same organisation, the business should establish an organisation-wide or business area specific threat assessment baseline (or baselines), and use them as input to all risk assessments. These baselines will need to be amended if the threat landscape changes, or if something significant changes within the organisation
Vulnerability
Vulnerability is a weakness which can be exploited by a threat to deliver an impact. A system or service could be compromised through the exploitation of vulnerabilities in people, places, processes or technology.
When assessing their risks, organisations should ensure that they have a clear and realistic understanding of where and how their systems and services are vulnerable. Whilst organisations can’t control the threats they face, they can reduce their vulnerabilities.
Impact
Impact describes the consequences of a risk being realised. To allow risk evaluation and prioritisation, impact should specify the negative effect that a risk’s realisation would entail.
This should include expected losses (eg financial and reputation losses) as well as business objectives which would not be achievable as a result of the impact. Organisations can exercise control over the negative impact that realisation of a risk would have, and should plan for this to happen.
Other inputs
Some risk assessment methods also consider likelihood and asset values as components of risk and inputs to assessments.
Likelihood estimates how likely it is for a threat to occur. It can be captured by examining historical records of compromises to estimate how history will be repeated. Some methods draw on likelihood to help determine vulnerability. Note that metrics of past occurrences are not necessarily a useful indicator of what will happen in the future.
Asset values are used to provide an understanding of what systems, services, information or other assets the organisation really cares about. This insight will provide organisations with a view of what it is they really want to protect. The HMG Security Policy Framework (SPF) mandates that Government organisations assign asset owners to critical business assets, who are responsible for valuing those assets, and making risk informed decisions on how those assets are used. Asset valuations are a key consideration when determining the impact input for risk assessment purposes.
Risk assessment output
Irrespective of the risk assessment method used, the output should be meaningful, understandable, realistic, and in context so that it informs risk management decisions and cannot be interpreted in different ways by different people
The level and type of detail provided by the output (ie technical or not) will be dependent on who the risk assessment is for and what risk management decision it is meant to inform.
Understand what risks exist
To understand what risks exist, the chosen risk assessment method should be applied in the context of what the organisation is trying to achieve. To do this, you should know:
- which risk management decisions the assessment will inform?
- who is responsible for making them?
- what level of detail is needed?
Before conducting a risk assessment, the organisation needs to decide and agree how risk assessment output will be presented. There is little value in a risk analyst producing a large and detailed risk assessment document, when the decision maker will only read the first page. Ensure that the scale and rigour of analysis performed (and the amount of documentation produced) matches the business context and is justified and proportionate.
The output of any risk assessment should be recorded for traceability purposes.Traceability is important so that risk management decisions and investment choices can be traced to an identified risk.
Prioritise the output from a risk assessment to allow the organisation to make informed risk management decisions. Any prioritisation of risk should be based on a meaningful understanding of what the organisation really cares about, not meaningless risk level boundaries.
Communicate risk consistently
Irrespective of the approach taken to assessing risks, the outcome should be captured in a way that can be used to inform business decision making. Output from risk assessment and other risk management activities may also need to be communicated to interested third parties.
The results of risk assessments depend largely on the experience and biases of the individual conducting them. As a result, it is difficult to obtain consistent risk assessments from different risk practitioners even when applying the same method. Consistency in risk assessment and risk management is important to enable effective decision making and communication. Consistency does not come from the repeated application of a specific risk assessment method. Consistency is achieved by ensuring that:
- the inputs to and outputs from assessments are meaningful in the context of what the business is trying to achieve
- risk professionals do not go about their work in isolation but collaborate with the wider organisation to achieve a consistent view of the business context
Different organisations do not have to use the same risk assessment methods in order to communicate risk consistently, provided they use a common language that describes the inputs to and results of their risk assessment and risk management activities. What common language is used is a matter for organisations to agree amongst themselves.
Agreeing how to communicate will create trust amongst a community who need to have confidence in the decisions made by others. Organisations should, as a minimum, be able to communicate:
- the threat context under which risk assessments have been conducted
- the willingness of their organisation to accept risk
- the status of managed risks, and what any risk valuations actually mean
- what control measures have been taken and how much rigour has been applied to managing risks within the organisation
You should also:
- avoid situations where (for example) both organisations articulate risk in terms of levels, but the actual meaning of these levels in each organisation differ
- communicate risk to third party delivery partners by reflecting real and meaningful risk management requirements in contracts and service level agreements; it is not sufficient to say in a contract or agreement that a system or service must be accreditable or compliant with the requirements of a particular standard
- ensure that security requirements in contracts and agreements are informed by and traceable to real risks or external requirements whilst being communicated in a meaningful and testable way.This will ensure that so that there is a shared understanding between consumer and provider of what outcome is required
Make informed risk management decisions
Throughout the lifecycle of a system or service, the organisation will need to make objective decisions about what needs to be done to manage identified risks. This should be based on a clear and meaningful understanding of risk.
These decisions should be informed and supported by information, subject matter expertise and evidence. It is for the organisation to decide how much and what form of information is required, together with the level of expert advice and evidence needed to demonstrate that risks are being managed.
Examples of information and evidence that could be used to support risk management decisions include:
- statements from the organisation on what risks it will and will not take to achieve its objectives
- the output of a risk assessment in the context of what the organisation is trying to achieve
- a description of the security controls that are already in place (or those that are needed to manage the identified risks)
- the cost of controls needed to manage a risk
- evidence and information on how third parties are managing risk and any contractual considerations that could affect the decision
- evidence that provides confidence that security controls have been implemented to manage identified risks
- evidence that provides confidence that security controls will continue to manage risks throughout the whole lifecycle of the system or service
- a view of the status of risks after they have been managed
It is important that the organisation understands what effect its risk management actions have on the risks it has identified. The organisation must be capable of communicating this to partners or authorities as necessary.
Residual risks
It is not possible to say that a system or service is ‘risk free’, or 100% secure. After risk management action has taken place, some risks will remain. These are often referred to as residual risks.
Some risk management approaches estimate how much a specific risk management action reduces an identified risk from its original state. For example, a risk management action may reduce a risk from high to medium. It is not possible to quantify the level of risk reduction as a result of a single or suite of security controls, and basing risk management decisions on estimates of risk reduction can encourage a false sense of security.
As a minimum, it is better that organisations understand and be able to communicate:
- which risks are being actively managed
- how they are being managed
- the confidence the organisation has that measures are effective
- any risks that are not being managed at all
An illustration on how to apply good risk management
The following case study illustrates at a high level how the Managing information risk guidance can be applied. It is not intended to be a full and comprehensive application of the guidance.
Start by understanding the business context
This business context must be provided by the organisation. It is not something that should be left to a risk assessor or analyst to work out for themselves in isolation.
What is the organisation trying to achieve?
In this case study, a government organisation wants to enable its customers to register for residents’ parking permits over the Internet. The organisation’s IT department has been tasked with delivering an online service that will provide customers with the ability to register for parking permits.
The Head of IT is responsible for the successful delivery of the service, and the Head of Public Services has been identified by the organisation as being responsible for the security of the service, and for making risk management decisions.
What is important to the organisation?
Customer records have been identified as an important information asset involved in the delivery of the service and the Customer Data Manager is the information asset owner for these assets. The Customer Data Manager has been asked to describe what aspects of them the business cares about, resulting in the following statements.
- an unauthorised release of customer records could result in damage to the privacy and financial well-being of our customers and to the reputation of the organisation. This would need to be reported to the Information Commissioners Office (ICO), potentially resulting in financial penalties
- any unauthorised change to, or error in customer records could result in damage to the privacy and financial well-being of our customers, to the reputation of the organisation, and its compliance with legal and regulatory requirements. This could result in financial penalties and reduced customer confidence in the service and the organisation
- a loss of customer or service access to customer records would cause no physical harm to anyone. A loss of one day could cause minor distress and inconvenience to customers and partners, but could be managed within the customer services department. However, a loss of more than one day would cause inconvenience to customers and reputational damage to the organisation that would need to be managed at board level
What risks will and won’t the organisation take?
The Head of Public Services has agreed the following statement with the organisation about what risks it will and won’t take with regard to the use of technology to deliver online services to customers.
The organisation will make use of technology solutions to realise the benefits of registering parking permits without the need for physical outlets. However, risks that result in the following outcomes will not be accepted:
- harm to the physical well-being of customers and employees
- harm to the financial well-being of customers and employees
- breaches of the organisation’s legal or regulatory responsibilities
- widespread damage to the reputation of the organisation
- costs or financial damage to the organisation
Decide on the risk management approach
The organisation needs to demonstrate that it meets the mandatory security outcomes as described by the HMG Security Policy Framework (SPF). It will therefore manage risks to its information, technology and services by developing and communicating a set of security policies and procedures for the service by taking account of the latest HMG advice and guidance on the security of online services.
The organisation would like to use common solutions to technology problems where available, but at this time there is no common solution available. The organisation therefore needs to conduct its own risk assessment activity to inform risk management decisions.
The organisation already has ISO/IEC 27001 certification for a number of its business areas. Within the scope of those certifications are existing IT systems, and the organisation is used to assessing what it does in the context of the controls provided by the standard. A decision has therefore been made that applicable security controls from the standard will be applied to the service.
Confidence that security has been appropriately implemented and maintained and that security policies and procedures are working as expected will be gained by:
- ensuring that the Head of Public Services has been involved in all key security decisions from the outset of the project
- independent audit and security testing of the service before going live, and periodically throughout its operational lifetime
Choose the right risk assessment method
At this point in the project, the organisation has decided to undertake an initial risk assessment that is consistent with the high-level risk assessment approach described by ISO/IEC 27005. This approach takes threat, vulnerabilities and impact as inputs into a qualitative assessment of risks to the online service.
To achieve this, the Head of Public Services has employed a technology and information risk subject matter expert to assist in the identification, assessment, documentation and prioritisation of risks. A more detailed risk assessment may follow as the project progresses to provide a more thorough understanding of risks and what needs to be done to manage them.
Understand the key components of risk
Threat
The organisation has conducted an in-house threat assessment based on externally provided information and local security history. The assessment was carried out by security and business delivery experts and is being used as a baseline for threat for all risk assessments. The following extract is provided in the context of the online service under consideration.
Organised crime groups are interested in stealing and changing customer records and have attacked them in the past by attempting to fool employees into revealing customer details, or by mounting technical attacks on the services offered online to customers.
Vulnerabilities
The organisation has used a security subject matter expert working closely with technical and business experts to develop a view of vulnerabilities that may be exploited and is monitoring the services it provides to detect misuse. The following is an extract from that vulnerability assessment.
The system uses commercially available products and is connected to the Internet and other partner systems. Un-patched flaws in applications and systems could be exploited to gain unauthorised access to information assets.
Impact
To specify the negative effect realised by the organisation (if a specific vulnerability is successfully exploited), the risk analyst has referred to asset valuations that have already been assigned by the organisation. In this case the valuation was provided by the owner of the customer records asset. The following is an extract from that asset valuation that is relevant to the vulnerability under consideration.
An unauthorised release of customer records outside of the organisation could result in damage to the privacy and financial well-being of our customers and to the reputation of the organisation. Any compromise of confidentiality of customer records would need to be reported to the ICO and could result in financial penalties.
Understand what risks exist
Pulling it all together to identify risks
To bring the assessment together, the risk subject matter expert has taken account of and analysed the threat, impact and vulnerabilities to identify a number of risks that are relevant in the context of the online service. The following extract shows a meaningful risk using the organisation’s chosen risk assessment method.
Using the Internet, serious and organised crime could exploit known vulnerabilities in the commercial applications used to deliver online services to steal personal information. If realised, this could lead to damage to the privacy and financial well-being of our customers, fraud, a breach of legal or regulatory responsibilities and damage to the reputation of the organisation.
Prioritising the resultant risks
It is now necessary to prioritise identified risks for management purposes. This prioritisation should be carried out in the context of the organisation and what it cares about.
In this case the organisation has made the following statement:
The organisation will make use of common technology solutions to realise the benefits of registering parking permits without the need for physical outlets. Risks that result in the following outcomes will however not be accepted:
- harm to the physical well-being of customers and employees
- harm to the financial well-being of customers and employees
- breaches of the organisations legal or regulatory responsibilities
- widespread damage to the reputation of the organisation
- costs or financial damage to the organisation
The example risk that we have identified, if realised, would result in “damage to the privacy and financial well-being of our customers, a breach of legal or regulatory responsibilities and damage to the reputation of the organisation.” In the context of what the organisation has said it cares about, this risk would clearly be a high priority for the organisation to manage.
Communicate risk consistently
To achieve consistency of assessment, the organisation has decided to use the output from the threat, vulnerability and impact assessments as baseline input to all risk assessments carried out for online services. These inputs will be reviewed and updated if necessary every six months as a matter of routine, or when a significant change occurs to the threat or technology landscape (such as a technology vulnerability becoming known, or new attackers targeting the organisation).
In terms of communicating with partners, the following information will be provided to organisation partners who need confidence that risks have been appropriately managed.
The online service provides customers with the ability to register parking permits over the Internet. The service will store and process OFFICIAL information.
The threat posed to the service by serious and organised crime groups has been assessed, and identified risks are being managed through application of appropriate ISO/IEC 27002 security controls.
(In the context of the example risk provided here, the controls aimed at keeping applications, operating systems and firmware patched and up to date would be appropriate.)
The organisation will not accept any risk that results in harm to the finances of customers or employees, breaches in legal or regulatory responsibility, or damage to the finances and reputation of the organisation.
The service has been designed and implemented to protect against those threats identified by the threat profile for OFFICIAL. Security policies and procedures are in place to support the continuous management of technology and information risks relating to the online service, and there is an ongoing regime of independent audit and testing to provide continued confidence in the measures that have been applied.
Though controls have been implemented to manage risks regarding known technology vulnerabilities, there remains a risk that an unknown technology vulnerability maybe exploited to cause harm to the service and its customers.
Make informed risk management decisions
The Head of Public Services:
- will make risk management decisions about the security of the online service, based on the risks resulting from a risk assessment that has been conducted in accordance with ISO27005 (and a clear understanding of what the organisation wants to achieve)
- will engage with the IT department’s delivery team throughout the project and ensure that decisions are made available in a timely way so that the service is delivered on time
- will ensure (once the service is operation) that risk management will be continuously applied throughout the whole lifecycle of the service
Decision making do’s and don’ts
The following document contains a simple set of ‘do’s and don’ts that can help risk assessment and risk management decision making.
