Government response to the call for views on consumer connected product cyber security legislation
Published 21 April 2021
1. Ministerial foreword

Matt Warman MP, Minister for Digital Infrastructure
The COVID-19 pandemic has highlighted the paramount importance of science and technology in our society. Whether it be working remotely, securing our homes, or even keeping in touch with loved ones, connectivity has become a part of our daily needs.
This government is unashamedly pro-tech and deeply values the benefits that technology and greater connectedness can bring. The innovations that have allowed an increasingly diverse range of consumer products to connect to the internet are no exception to this. And despite rapid technological progression, and increasing uptake, we are only scratching the surface of the advantages that connected products could offer consumers and businesses, as well as the wider economy.
As part of our work to make the UK the safest place to be online, we have to be able to assure consumers that the devices being brought into their homes are secure - technological advancement cannot be at the expense of consumer security.
That is why we have already encouraged industry to take action. Whilst some progress has been made in implementing basic security features in these products, I fully understand that there is still more for us to do to protect citizens, increase consumer confidence and enable connected technologies to flourish sustainably.
The call for views on regulatory proposals that I launched in July 2020 was the latest in a series of efforts to tackle this issue by working collaboratively with industry, academics, civil society, and international partners. I would like to thank the individuals and organisations that took the time to share their views on the government’s proposals. The supportive and constructive feedback received in this exercise has played an important role in further refining our legislative ambitions, which we are committed to introducing when parliamentary time allows.
Today, I’m excited to share the government’s response to the call for views and further details of the world-leading legislative framework that we’ve been developing. This represents a key milestone in bringing us one step closer to being able to harness the opportunities presented by connected products, safe in the knowledge that this isn’t at the expense of security.
Matt Warman
Minister for Digital Infrastructure
2. Executive summary
Internet connected products that have universal default passwords, are not updated against known security flaws, or are otherwise designed without security in mind pose a serious threat to individual privacy and security. These products also pose a wider threat if a malicious actor takes control and uses them to attack others including businesses, government and infrastructure. With more and more consumer connected products being purchased, we need to act to ensure that consumers are protected.
The government has been working with the tech industry to better secure consumer connected products for several years. In 2018 we published a Code of Practice, setting out the security principles that should be applied by manufacturers and other relevant industry stakeholders. Since then we have been continuing discussions with industry on how to ensure the code is applied, and have been engaging internationally to persuade other states to adopt better security. In 2020, a new European Standard on connected product security, EN 303 645[footnote 1], was adopted, with the UK government contributing significantly to its development. Similar standards are now being adopted across the world.
Now that internationally accepted standards are in place, the government believes that the time has come to start to enforce these standards. Too many insecure consumer connected products remain on the market and we need to take steps to ensure that in future, consumers can use these products with confidence.
Whilst consumer products (including consumer connected products) are already subject to a regulatory framework in relation to safety and environmental requirements, in particular the Electrical Equipment (Safety) Regulations and Radio Equipment Regulations, new regulation is needed to ensure that products made available to UK consumers comply with a minimum baseline level of cyber security.
From 16 July 2020 to 6 September 2020, the government ran a call for views on proposals for UK domestic legislation to regulate the cyber security of these products, rendering products like televisions, cameras and household appliances which connect to the internet safer and more secure for people to use.
The government will now legislate, when parliamentary time allows, to create a new robust scheme of regulation to protect consumers from insecure connected products. The regulation will apply to all consumer connected products such as smart speakers, smart televisions, connected doorbells and smartphones. A number of devices will be exempt due to the specific circumstances of how they are constructed and secured, including desktop computers and laptops. The security requirements will align with international standards and are familiar to all manufacturers and other relevant parties across the industry. An enforcement body will be equipped with powers to investigate allegations of non-compliance and to take steps to ensure compliance.
This legislation, which will apply across the whole of the UK, will protect consumers at home, but also demonstrate our continued global leadership in cyber security. In 2016 our objective within our National Cyber Security Strategy was that the majority of online products and services coming into use become ‘secure by default’ by 2021. We have seen successes through the publication of our Code of Practice, and the adoption of these thirteen principles abroad and within globally applicable standards from international standards bodies. However, aspects of industry still persist in using out-of-date and dangerous practices (such as universal default passwords), and the risk to consumers can no longer be tolerated. Our proposed legislation will further close the door on insecure technology.
This document provides an overview of the government’s updated policy intentions for the proposed legislation to regulate the cyber security of consumer connected products, whilst also summarising the feedback the government received on its call for views on regulatory proposals in this space, as well as detailing the government’s response to the feedback received.
3. Policy objectives
3.1 Protecting citizens, networks and infrastructure from harm
As the growth within the consumer connected product sector outpaces the adoption of good practice, the attack surface is continuing to grow, meaning more people are more vulnerable to a more diverse range of harms. The average UK household is estimated to have had over nine smart devices in 2020, and forecasts expect up to 50 billion connected devices worldwide by 2030 (Statista, 2020). The way in which we use these products will continue to evolve with changes in lifestyle and home-working arising from COVID-19, and the increasingly widespread adoption of 5G technologies.
With this in mind, DCMS commissioned a report from The PETRAS National Centre of Excellence for IoT Systems Cybersecurity, a partnership of 12 universities, including University College London who led on the production of the report. This report focussed on areas of potential emerging risk within the consumer “internet of things”(IoT) landscape and acknowledges the proactive approach taken by DCMS in improving the security of IoT devices for consumers, but also highlights the importance of looking forward and identifying new risks.
3.2 Enabling emerging tech to grow and flourish by improving security, and Increasing consumer confidence
The consumer connected product sector has been forecast to grow for decades, with the lack of effective cyber security measures often cited as the key barrier to it reaching its full potential. In a DCMS commissioned study published in 2020, 28% of respondents were not planning to buy a consumer connected device in the next twelve months owing to security concerns. Since the emergence of the Mirai malware (2016) and its variants, there have been frequent high profile attacks and consumer reports illustrating how sensitive information can be taken from segments within the “internet of things”
3.3 Adopting a proportionate approach to placing obligations on relevant economic actors, without compromising effectiveness
Since the government first started considering intervention in this space in 2016, it has deliberately adopted a consultative and collaborative approach with industry, academia, subject-matter experts, and other key stakeholders. Contributions from affected stakeholders have continued to play a critical role in developing the government’s legislative intent, including through a May 2019 Consultation and a July 2020 call for views. A primary aim of this approach has been to ensure that interventions in this space are maximally effective whilst minimising impact on organisations involved in the manufacture and distribution of consumer connected products.
3.4 Continuing to protect citizens, networks and infrastructures from harm in the face of an uncertain future
To remain effective, the government’s intended legislation will need to be able to adapt in the face of rapid technological advancement, the evolving techniques employed by malicious actors, and the broader international regulatory landscape.
4. Overview of the government’s intent
4.1 Key policy positions
The desired outcome of the government’s intervention in this space is that the range of harms that can arise from vulnerable consumer connected products are minimised. We will look to achieve this by ensuring that products within the scope of our proposed regulation that do not comply with a minimum baseline level of cyber security are not made available to UK consumers. Our planned legislation will place obligations on relevant economic actors, and establish a robust enforcement regime to achieve this outcome.
Twelve key policy positions underpin the government’s intended regulatory approach. These represent the culmination of years of collaboration with the National Cyber Security Centre, international partners, industry, academia, cyber security experts, and civil society in developing world-leading legislation in this space.
4.2 Key policy positions - scope of the intended legislation
| 1 - Defining products in scope | 2 - Exempted product classes |
|---|---|
| The intended legislation will apply to any network-connectable devices and their associated services that are made available primarily to consumers, except products that are designated as out of scope. | Specific product classes that would otherwise fall within the scope of this legislation, but for which it would be inappropriate for it to apply to, will be exempted from the legislative framework. |
| 3 - Adaptable scope | 4 - Interoperability |
| Where changes to the wider regulatory, technological, or threat landscapes render it appropriate, the intended legislation will allow Ministers, subject to agreement by Parliament, to adjust the scope of consumer connected products covered by this regulation by updating the list of specific product classes exempted from its effects. | The government will ensure that the intended legislation is interoperable with other existing or planned government interventions covering contiguous, or overlapping product classes, such as BEIS commitments to regulate smart appliances. |
4.3 Key policy positions - role of economic actors
| 5 - Obligations on economic actors | 6 - Security Requirements |
|---|---|
| The legislation will place proportionate obligations on relevant economic actors involved in the transmission of in scope products to consumers to ensure that insecure products are not made available to UK consumers. | The legislation will obligate relevant economic actors to not make consumer connected products available on the UK market unless they comply with certain security requirements, or designated standards. |
| 7 - Adaptable security requirements | 8 - Product Assurance |
| Where changes to the wider regulatory, technological, or threat landscapes render it appropriate, the intended legislation will allow Ministers to update the security requirements and designated standards that relevant economic actors must ensure products made available on the UK market comply with. | Where changes to the wider technological or threat landscapes render it appropriate, the intended legislation will enable Ministers to mandate product assurance for particular categories of consumer connected products. |
4.4 Key policy positions - how the legislation will be enforced
| 9 - Enforcement authority | 10 - Enforcement role and responsibilities |
|---|---|
| An enforcement authority will investigate non-compliance, take action in relation to any non-compliance, and provide support to relevant economic actors to enable them to comply with their obligations. | To enable proportionate enforcement across a range of contexts, the legislation will equip the enforcement authority with necessary powers, as well as the ability to issue appropriate corrective measures, sanctions and potentially in the most serious circumstances, to bring forward criminal proceedings. |
| 11 - Appeals | 12 - Proportionate transitional provisions |
| Relevant economic actors will have the right to appeal any sanctions or corrective measures brought against them, in a manner consistent with the processes used in existing product safety legislation. | Following royal assent, the government will provide relevant economic actors with an appropriate grace period to adjust their business practices before the intended legislation fully comes into force. |
How to read this document
Where necessary to best communicate our intentions, and to better contextualise the government’s position, indicative policy and technical details have been provided. It should be noted however, that the process of translating the government’s final policy intentions into a legal text is ongoing, and that the exact legislative mechanisms that will ultimately best serve the government’s policy intentions are still being determined.
This indicative detail should not be interpreted as final legislative text, or representative of what the legislation would look like when brought into force.
4.5 Key policy positions - scope of the intended legislation
Key Policy Position 1 - Defining products in scope
The intended legislation will apply to any network-connectable devices and their associated services that are made available primarily to consumers, except products that are designated as out of scope.
The government intends to navigate the inherent challenges of defining consumer connected products exhaustively, by adopting a broad definition of network-connectable products that fall within the scope of this regulation, and specifying product categories out of scope as necessary. Broadly, our intentions are to define “consumer connected products” in a way that achieves the following outcomes:
-
Includes only products that are intended to be used by consumers, or products that are likely to be used by consumers in reasonably foreseeable conditions, and excludes products that are only used by businesses or in industrial settings (although products that are primarily used by consumers, but can also be used in a business environment, such as Smart TV’s or connected security cameras, would be included)
-
Includes only products that have a network interface (e.g. can communicate data via Wifi, Bluetooth, data cable etc.)
-
Includes both devices and their associated services (where “product” is understood to refer to both of these). Some of our security requirements will apply to only the device, some apply to both the device and associated services. Associated services would not include 3rd party apps that may also run on the device (e.g. Netflix on a smart TV).
-
Includes “ancillary” products that connect primarily to other devices
The non-exhaustive list in Box 1 contains examples of products that the government intends to capture in the scope of this legislation:
Box 1 - Non-exhaustive list of products within the scope of the intended regulation
- Smartphones
- Connected cameras, TVs and speakers
- Connected children’s toys and baby monitors
- Connected safety-relevant products such as smoke detectors and door locks
- Internet of Things base stations and hubs to which multiple devices connect
- Wearable connected fitness trackers
- Outdoor leisure products, such as handheld connected GPS devices that are not wearables
- Connected home automation and alarm systems
- Connected appliances, such as washing machines and fridges
- Smart home assistants
It should be noted that the government does not currently plan to include Operational Technologies, such as industrial connected products, within the scope of this legislation. Wherever practical, government intends for this legislation to apply to all activity that could lead to vulnerable products being made available to consumers, including consumer connected products that are:
- both free of charge and paid for;
- sold in shops both online and offline;
- offered as incentives or free sign up gifts as part of a contract or offer/promotion;
- In exchange for promotion;
- financed products that a consumer will own once all payments have been made;
- made available as part of an insurance contract; and
- traded for another good or service.
Key Policy Position 2 - Exempted product classes
Specific product classes that would otherwise fall within the scope of this legislation, but for which it would be inappropriate for it to apply to, will be exempted from the legislative framework.
Whilst the government’s ambition is to capture most consumer connected products within the scope of this regulation, we are also committed to ensuring that businesses are not subject to an unnecessarily duplicative regulatory regime. Some product categories that fall within the intended definition of consumer connected products, such as Smart Meters are already subject to robust regulation. Similarly, the cyber security of some other consumer connected products, such as certain categories of Automotive vehicles will be covered by future regulation particularly relevant to that product category. The government’s intention is to exempt these categories of consumer connected products from the scope of the planned legislation at commencement.
Products that the government has deemed inappropriate to include pending further investigation, such as desktop computers, laptops and tablets without a cellular connection, will also be exempted from scope at the point the legislation is commenced. Our July 2020 call for views on earlier legislative proposals proposed that all conventional IT products be covered by this regulation, but we recognise the unique challenges that manufacturers of these products would face in complying with our legislation, and will conduct further engagement and analysis work before taking any action to add these devices to the scope of the regulation in the future.
Products where inclusion would impose impractical obligations on businesses disproportionate to the likely benefits will also be exempted from scope at commencement. This chiefly applies to second-hand products. Lacking a direct business connection with the manufacturer, it would not be practical for economic actors involved in the distribution of second-hand products to meet the obligations the intended legislation would place upon them.
The product categories that would otherwise fall under the intended definition of consumer connected products, but will be exempted at commencement, are summarised in Box 2.
Box 2 - Consumer connected product classes explicitly exempted from the intended legislation from commencement
Products for which security is already covered by existing regulation or planned future regulation
- Smart Meters
Products that the government deemed inappropriate to include until additional engagement and analysis has been conducted to further assess business impact
- Laptops and desktop computers, Tablets without a cellular connection
Products where inclusion would impose impractical obligations on businesses
- Second-hand products
Key Policy Position 3 - Adaptable scope
Where changes to the wider regulatory, technological, or threat landscapes render it appropriate, the intended legislation will allow Ministers, subject to agreement by Parliament, to adjust the scope of consumer connected products covered by this regulation by updating the list of specific product classes exempted from its effects.
The government intends for this legislation to allow Ministers to specify product classes exempted from scope using an agile mechanism such as secondary legislation. To ensure that this legislation remains effective amidst changes to the wider regulatory, technological, or threat landscapes, in instances where the balance of expert advice, robust analysis, and proportionate engagement leads Ministers to the conclusion that the scope of products captured by this regulation must be modified, the intended legislation would also enable Ministers to manage the product exemption list, including adding product classes (removing these products from scope) and removing product classes (bringing these products into scope).
The government also requires the ability to align the scope of these regulations with evolving cyber security requirements that already cover certain product classes through other legislation (e.g. network-connectable devices solely for medical purposes). In the earlier proposals we sought feedback on in our July 2020 call for views, the government was intending to initially exempt a number of additional product categories from this legislation, including automotive vehicles, smart charge points for automotive vehicles and medical devices. As a result of changes to the regulatory landscape concerning these products since the publication of our call for views, the government has been exploring the possibility of the intended legislation also capturing consumer connected products in these categories at some point in the future. The government will engage further with relevant industry stakeholders on the matter before bringing any additional products into scope.
Key Policy Position 4 - Interoperability with the wider regulatory landscape
The government will ensure that the intended legislation is interoperable with other existing or planned government interventions covering contiguous, or overlapping product classes, such as BEIS commitments to regulate smart appliances.
The rapid pace of technological innovation and the inherent challenges of maintaining effective regulation in the face of this change, necessitates concerted action by government to ensure that contiguous government interventions are compatible with each other.
To this end, officials developing the intended legislation have been engaging with colleagues both from across government, as well as with international partners, to ensure that the intended legislation works synergistically with existing and future regulatory interventions of relevance, including existing legislative frameworks where possible.
We have been working to ensure that our intended legislation is compatible with the Department for Business, Energy & Industrial Strategy commitment to regulate smart appliances, including their interoperability, data privacy and cyber security, recently detailed in the December 2020 Energy White Paper.
4.6 Key policy positions - role of economic actors
Key Policy Position 5 - Obligations on economic actors
The legislation will place proportionate obligations on relevant economic actors involved in the transmission of in scope products to consumers to ensure that insecure products are not made available to UK consumers.
A key objective of the intended legislation is to ensure that no consumer connected product enters the UK market unless it incorporates basic cyber security measures. The government will place various obligations on relevant economic actors involved in the manufacture and distribution of these products to ensure that this objective is achieved.
The intended legislation will obligate manufacturers to not place consumer connected products on the UK market unless they comply with specific security measures, outlined in legislation through security requirements or designated standards.
The legislation will also obligate manufacturers to publish a publicly available declaration of conformity, to take action if they place a product on the market that is not compliant with the security requirements or designated standards, and to cooperate and comply with the appointed enforcement authority in such instances.
To ensure that all products made available to consumers are captured, including products made by manufacturers based outside of the UK, certain manufacturer obligations will fall to either the manufacturer’s authorised representative, or the importer of the product to the UK should the manufacturer lack an authorised representative, should an appropriate authorised representative or importer exist.
Economic actors involved in the distribution of in scope products to consumers, including wholesalers and retailers, will also be obligated to play a role in protecting consumers and the wider economy from insecure consumer connected products. Obligations on these entities will include a requirement to verify that the manufacturers of consumer connected products they are involved in the transmission of have published a declaration of conformity, and to cooperate and comply with any enforcement activity.
Key Policy Position 6 - Security Requirements
The legislation will obligate relevant economic actors to not make consumer connected products available on the UK market unless they comply with certain security requirements, or designated standards.
We intend to create two routes to conformity within the intended legislative framework:
-
The first route is to implement the security requirements as detailed in legislation. These initial security requirements have been derived from and align with the top three guidelines from the Code of Practice for Consumer IoT Security, and key provisions within ETSI European Standard (EN) 303 645.
-
As a second alternate route to conformity, we intend to designate relevant standards that can be implemented in lieu of the security requirements in legislation. Specific provisions/clauses of standards will be designated so that implementation of these achieves the same (or nearly the same) as implementation of the security requirements. This will enable us to facilitate alignment across jurisdictions.
Box 4 - Summary of security requirements and designated standards
| Security Requirement | Explanation of intent | Designated external standards |
|---|---|---|
|
Security Requirement 1 Ban universal default passwords |
Our intent is to cover all passwords within the device, including those not normally accessible by the user, such as passwords on administrative interfaces, or within firmware of sub-components. Pre-installed software applications (Apps), including those that are 3rd party provided but pre-installed on a device, are also in scope. Our intent is also to ban passwords which may be unique per device, but are still easily guessable and therefore still present a risk (for example, if incremental counters are used such as ‘password1’, ‘password2’ and so on). | EN 303 645 provisions 5.1-1 and 5.1-2 |
|
Security Requirement 2 Implement a means to manage reports of vulnerabilities |
The intent of this requirement is to provide a transparent route for third parties to report vulnerabilities to the manufacturer, making it possible for security issues to be resolved. This practice remains uncommon for manufacturers of consumer connected products, however, this is an essential mechanism to identify and address security shortcomings, and to aid security innovation in the sector. Note: designated standards for this outcome must be applied to the device and associated digital services |
EN 303 645 provisions 5.2-1 OR ISO/IEC 29147(2018): clause 6.2 |
|
Security Requirement 3 Provide transparency on for how long, at a minimum, the product will receive security updates |
Providing security updates is one of the most important mechanisms to protect consumers. Their purpose is to address security shortcomings that place consumer’s privacy, data and security at risk and that are typically only identified, and able to be utilised, once the product is on the market. They also enable consumers to make better informed purchasing decisions. When buying a product, consumers need to be able to find out the minimum period of time for which that product will be supported with security updates. It should also be noted that the defined support period can always be extended unilaterally by the manufacturer. | EN 303 645 provision 5.3-13 |
Guidance on implementing security requirements
It is important that manufacturers and organisations in supply chains have the information they need to implement the requirements that we are setting out. In 2020 the IoT Security Foundation, an industry expert organisation, released freely accessible guidance based on these security requirements as well as on relevant guidelines of the Code of Practice for Consumer Internet of Things Security and relevant provisions of the ETSI EN 303 645. Various expert organisations including ETSI, GSM Association (GSMA), National Institute of Standards and Technology (NIST) and the International Organization for Standardization (ISO) also produce pertinent guidance materials.
Key Policy Position 7 - Adaptable security requirements
Where changes to the wider regulatory, technological, or threat landscapes render it appropriate, the intended legislation will allow Ministers to update the security requirements and designated standards that relevant economic actors must ensure products made available on the UK market comply with.
To ensure that the regulation continues to protect people and the economy from harm posed by insecure products, the intended legislation will allow Ministers to update the security requirements and designated standards using an agile mechanism, such as secondary legislation. This would be done in circumstances where such action was necessary to keep pace with changes to the wider regulatory, technological or thread landscapes. It may be necessary to introduce requirements in the future relating to (but not limited to) areas such as the following:
- User authentication
- Vulnerability reporting
- Software updates
- Protection of data at rest and in transit
- Security design principles for software and hardware
- Protection of personal data (privacy)
- Product and wider network resilience
- Provisions of information and guidance to product users
Key Policy Position 8 - Product Assurance
Where changes to the wider technological or thread landscapes render it appropriate, the intended legislation will enable Ministers to mandate product assurance for particular categories of consumer connected products.
Some responses to the call for views highlighted the importance of product assurance service in achieving good security outcomes. We recognise this and strongly encourage voluntary take-up of assurance services for consumer connected products. In the future, it may be appropriate to require certain categories of consumer connected products, especially where the risk to consumers is considered to be high, to undergo an assurance process (for example independent assessment or assisted self-assessment).
For that reason, the intended legislation will enable Ministers to be able to mandate assurance for designated categories of consumer connected products. We do not have the intention to make use of this power at an initial stage, and would only do so following engagement with industry and analysis of benefits and costs.
4.7 Key policy positions - How this legislation will be enforced
Key Policy Position 9 - Enforcement authority
An enforcement authority will investigate non-compliance, take action in relation to any non-compliance, and provide support to relevant economic actors to enable them to comply with their obligations.
A number of considerations, developed in line with government best practice on appraisal and evaluation, and on which feedback was solicited in the call for views, have been used to develop the methodology employed by officials to appoint the most appropriate enforcement authority for the intended legislation.
Key Policy Position 10 - Enforcement role and responsibilities
To enable proportionate enforcement across a range of contexts, the legislation will equip the enforcement authority with necessary powers, as well as the ability to issue appropriate corrective measures, sanctions and potentially in the most serious circumstances, to bring forward criminal proceedings.
Our intended approach will ensure that the enforcement authority has access to the tools, including a range of corrective measures and civil sanctions, that it needs to take action against non-compliant actors and remove the risk posed to consumers. The enforcement authority will ensure that more stringent measures are only deployed when voluntary measures have failed to achieve compliance, or when necessitated by the seriousness of an infraction.
We intend to ensure that the enforcing authority has access to a range of powers to enable them to investigate non-compliance in an effective and proportionate manner. These powers range from investigatory powers, including the power of search and entry, to information sharing powers. The necessary safeguards will be put in place to ensure powers are used with adequate oversight and to protect businesses from undue burden.
The enforcement authority will be able to serve a range of corrective measures and civil sanctions on non-compliant economic actors. Whilst the enforcement authority will initially attempt to resolve matters through voluntary measures, we believe it is necessary for the enforcement authority to have access to a proportionate suite of potential measures in order to efficiently deal with non-compliance across a range of circumstances. These sanctions will include forfeiture of goods and financial penalties.
Key Policy Position 11 - Appeals
Relevant economic actors will have the right to appeal any sanctions or corrective measures brought against them, in a manner consistent with the processes used in existing product safety legislation.
The intended legislation will incorporate an appeals process, aligned with those used in existing comparable product safety legislation to ensure that relevant economic actors have the right to appeal any sanctions or corrective measures brought against them by the enforcement authority.
Key Policy Position 12 - Proportionate transitional provisions
Following royal assent, the government will provide relevant economic actors with an appropriate grace period to adjust their business practices before the intended legislation fully comes into force.
The government remains committed to ensuring that businesses are given an appropriate amount of time to adjust their business practices before instances of non-compliance are actively enforced.
5. Call for views - analysis overview
The government reviewed and considered all feedback shared during the call for views response window (16th July - 6 September 2020), and this feedback has played an important role in shaping the government’s intended legislative approach in this space.
However, it should be noted the government is aware the balance of the feedback shared by individuals and organisations who elected to respond to the call for views may not be entirely representative of the wider population and business community, and has applied proportionate caution when interpreting the results. The government considered all feedback received in the call for views when shaping its intended regulatory approach.
Overall, the call for views received 110 responses. 74 responses came from organisations, and 36 from individuals. Of the organisational responses, the majority came from respondents who identified as “producers” of consumer smart products (24%), cyber security providers (24%) and “distributors”/sellers of consumer smart products (17%). Of the individual responses, the majority came from cyber security professionals (33%), followed by academics (22%) and professionals in other sectors (14%).
6. Call for views - questions
In addition to demographic information to aid in the analysis of feedback, the government requested that respondents consider thirteen questions related to different aspects of its regulatory proposals (questions 10 - 22 in the feedback survey). Where appropriate, summaries of the feedback provided for each of the questions, alongside government responses to this feedback, are detailed in the remainder of this document.
Scope of regulation questions
Q10 - To what extent do you agree or disagree that the following categories of conventional IT products (Laptops, PCs, and Smartphones) should be included within the scope of the proposed regulation?
Summary of responses (Q10)
Q10a - Laptops
| Strongly disagree | Somewhat disagree | Neither agree/ disagree | Somewhat agree | Strongly agree |
|---|---|---|---|---|
| 28% | 2% | 8% | 13% | 49% |
Number of likert scale responses: 53
45 respondents provided qualitative feedback to this question. Whilst a greater proportion of respondents overall agree that laptops should be in scope, the most common theme from the qualitative feedback highlighted that laptops are designed differently to other consumer smart products and that it would be very challenging for laptop manufacturers / “Producers” to ensure all components within the device met the security requirements. The second most popular response was that all internet connected devices should be in scope. Some respondents highlighted that laptops are used for sensitive tasks, such as work and storing and processing sensitive information. It was also highlighted that conventional IT should be included in order to maintain consistency and avoid creating fragmentation in the market.
A range of other themes were also identified across the responses, including that:
- laptop hardware is separable from its software;
- including laptops in scope doesn’t align with other regulatory efforts or standards;
- laptops have better security built in than consumer IoT and receive updates which are easier to implement due to user interfaces; and that
- laptops are commonly used and regulation would help to improve security.^
Q10b - PCs
| Strongly disagree | Somewhat disagree | Neither agree/ disagree | Somewhat agree | Strongly agree |
|---|---|---|---|---|
| 29% | 2% | 10% | 13% | 46% |
Number of likert scale responses: 52
44 respondents provided qualitative feedback to this question. Consistent with the feedback from 10a, more respondents who answered Q10b agreed with including PCs in the scope of regulation than disagreed. However, the most common theme from qualitative feedback was that PCs are designed differently to other consumer smart products and that including them in scope may therefore present challenges. PC hardware and software is far more customisable than other connected products making them very different in design and form from other off the shelf consumer connected products that are more generally manufactured on a one size fits all production line.
Some respondents emphasised that the security of these devices was important, as PCs are used for work and accessing sensitive information, such as personal data. Some respondents said that PCs are commonly used and that all internet connected devices should be in scope. On the other hand, some respondents said that PCs are used for more diverse purposes than consumer IoT, that their inclusion in the scope is not aligned with other regulation or standards, and that PC hardware and software is more separable.^
Q10c - Smartphones
| Strongly disagree | Somewhat disagree | Neither agree/ disagree | Somewhat agree | Strongly agree |
|---|---|---|---|---|
| 21% | 4% | 8% | 11% | 57% |
Number of likert scale responses: 53
43 respondents provided qualitative feedback to this question. Of the three categories (laptops, PCs, Smartphones), there was most support from respondents for smartphones to be included in scope. This was also consistent among those that provided a qualitative response. Some respondents said that smartphones should be in scope as they are very widely used. Several others responded that the security of these devices was important, as they are used for accessing personal information or work, while a number also thought that all internet connected devices should be in scope.
Some respondents thought that regulations would improve the security of these devices. Other respondents highlighted that this would not align with other existing regulations or standards.^
Government response (Q10)
Based on the feedback received in the call for views, as well as wider policy development, analysis, and engagement work, the government intends to include smartphones within the scope of this legislation.
Whilst the government still intends for all internet-connected products to be included in this legislation in the future, we recognise the unique challenges that the manufacturers / “Producers” of desktop computers and laptops may face in complying with this legislation as quickly as the manufacturers / “Producers” of other consumer connected products. The government recognises that PC hardware and software is more separable when compared to that of a smartphone. While smartphones are sold ‘off the shelf’, laptops and PCs are more likely to be sold to customer specification. The reconfiguration of laptops and PCs can sometimes be carried out by the same organisations involved in selling these products to consumers, further complicating the need to establish whether the final product meets baseline security measures.
Following feedback that we have received, our plans are to initially exclude laptops, desktop computers (“PCs”) and tablets without a cellular connection from scope. The government will engage further with industry before taking any action to add these devices to the scope of the regulation in the future.
Q11 - The ambition of this regulation is to establish a robust baseline across all smart connected products and to protect consumers and the wider economy from a range of harms. Please detail any unintended impacts that this proposed regulation would have, beyond the ambition stated above, to your organisation / the wider economy.
Summary of responses (Q11)
Q11a - Unintended impacts on ”Producers”
Of the 41 responses received, a number of respondents reported that introducing regulation to improve the security of connected devices would lead to rising costs for device “Producers”. Some others said that it would impact supply chains and may result in increased time to get products to market. Some also thought that it could distort competition in the market and disadvantage small “Producers”, while some others felt that there would be no impact on “Producers”.
One respondent suggested that it could affect devices which “are not specifically manufactured for use in the IoT ecosystem but may be used to enable IoT services”.
Q11b - Unintended impacts on “Distributors”
From the 32 responses received, there was a broad range of responses to this question. Some respondents reported that regulation may impact on “Distributor” supply chains. Some others thought that there would be additional costs or reduced sales as a result. Other less common responses included that respondents thought that “Distributors” wouldn’t be able to help customers with problems with their devices and that they would have to invest money into training to educate staff about the regulations. Another theme of feedback from some respondents highlighted that “Distributors” may have stock that they could no longer sell and there were concerns over a lack of clarity on the obligations of “Distributors”.
Q11c - Unintended impacts on other organisations
This question received fewer responses than others, with a total of 19, expressing a diverse range of views. Some respondents felt that there could be impacts on security researchers either through a lack of availability of insecure devices or the potential for legal action against researchers reporting vulnerabilities through a vulnerability disclosure policy. Others thought that there could be an impact on suppliers, including those that install connected devices, with one respondent suggesting that there could be an impact on organisations that loan connected devices.
Q11d - Unintended impacts on the wider economy:
Of the 29 respondents, some thought that costs could be passed on to the consumer through increased prices as a result of introducing regulation. Some respondents also raised concerns that individuals could import devices from unregulated markets. However, benefits of regulation were also highlighted, including the avoidance of cyber attacks and improved consumer confidence.
On the other hand, a small number of responses were concerned with potential issues such as increasing e-waste or legacy devices remaining in use or being sold at reduced prices before regulation is enforced.
Government response (Q11)
We appreciate the unintended impacts that our proposed legislation could have on the “Producers”, “Distributors”, and the wider economy. We remain mindful of the importance of adopting a proportionate approach to legislation in this space that protects citizens, the economy and infrastructure from the range of harms posed by insecure consumer connected products, without imposing excessive burdens on businesses.
The government has noted the feedback received in the call for views, and will publish a regulatory impact assessment detailing its assessment of the material costs and benefits of the intended legislation before it comes into force.
Q12 Please share your views on the suggested supplementary guidance to help businesses to implement the proposed security requirements (provided in section 4 - Obligations of the call for views). Are there any other forms of guidance you feel should be included?
Summary of responses (Q12)
There were a total of 40 responses which included a broad range of suggestions regarding additional guidance. These include suggestions for further guidance on products in scope including bluetooth products, security guidance including acceptable assurance and due diligence, guidance on how regulation will be applied to legacy devices, and guidance on how regulation will apply to second hand sales.
Some respondents also thought that guidance should be consistent with existing international standards.
Government response (Q12)
The government appreciates input from stakeholders about the guidance they would find helpful to accompany our legislation. We are finalising plans for developing guidance alongside our legislation, and will share further details ahead of legislation coming into force.
DCMS and NCSC have supported the Internet of Things Security Foundation (IoTSF) and Oxford Information Labs (OXIL) to develop guidance and webinars to support manufacturers / “Producers’’ in the implementation of the security requirements.
ETSI TC Cyber is developing document TR 103 621 which will provide guidance to help manufacturers / “Producers” and other stakeholders meet the provisions within EN 303 645.
Q13a - The proposed approach suggests using a broad definition of network-connectable product classes which could be in scope and specifying categories of products that are out of scope. Do you agree or disagree with this suggested approach?
Summary of responses (Q13a)
| Agree | Disagree | Don’t know |
|---|---|---|
| 54% | 44% | 2% |
number of agree / disagree / don’t know responses: 48
While a majority of respondents agreed with the suggested approach, 20 respondents indicated that they disagreed and elected to provide further written feedback. Of the respondents who disagreed, some thought that regulation should only apply to internet connected products, rather than “network connectable products” more broadly, while a small number of respondents felt that laptops, PCs and smartphones should be excluded. Some responses said that the scope should be aligned with existing international standards, with one referencing ETSI EN 303 645.
Q13b - Please share any views that you have on alternative wording, approaches, or ways to improve the proposed approach of using a broad definition of network-connectable product classes which could be in scope and specifying specific categories of products that are out of scope.
Summary of responses (Q13b)
There were a total of 32 responses to this question. Many respondents referenced existing or draft standards in their responses, such as ETSI EN 303 645, ISO/IEC 27402, ISO 27001 and IEC 62443-4-1, and related standards such as ISO 29147 and ISO 30111 in reference to vulnerability disclosure, EU Aviation Safety Agency (EASA) Decision 2020/006/R; and EASA Notice of Proposed Amendment 2019-07. A number of people felt that there needed to be more clarity around products that are included in the scope, whilst some others felt that certain devices and individual components (ie. non-finished products) should be out of scope.
Another respondent suggested that the definition could be “network-connectable or similarly digitally interfaceable” in order to clarify that devices which can “digitally interface” with network-connected devices are in scope. Other respondents referenced the term “connected device”, with one suggesting the definition used in Californian legislation (Senate Bill No. 327).
Government response (Q13a + Q13b)
We have explored alternative suggestions brought forward, but we remain confident that the approach outlined in the call for views, and detailed in our key policy positions on the scope of the intended legislation, is the right one, although it should be noted that the final technical approach to defining products in scope will ultimately be determined as part of the legislative drafting process.
The government’s intention is to base the requirements on international standards that were strongly supported by most respondents.
Q14 - Please outline any further feedback on the security requirements, as set out in section 3.3 of the call for views.
Summary of responses (Q14)
Q14a - Security Requirement 1 - Ban universal default passwords
Many of the 46 responses to this question expressed their agreement with this security requirement, with one noting that the requirement was an appropriate choice for regulation. Some added caveats to their support, which included supporting this requirement in lieu of phasing out passwords altogether in the future. Some thought that the security requirements should align with other international standards. Some respondents suggested that passwords should be banned altogether immediately, while others thought that all services on devices should have unique passwords, in contrast to the view that controlled access/age verification PINs should be out of scope.
Another theme mentioned by a small number of respondents was that an approach to specify the desired outcome should be taken, rather than to set out the requirement in specific detail in order to close any loopholes and futureproof legislation.
Q14b Security requirement 2 - Implement a means to manage reports of vulnerabilities
Of the 43 responses, a considerable number of respondents agreed with the second security requirement outright, with an additional group of respondents agreeing with caveats, which formed an overall majority in favour of the requirement. A common theme was that security requirements should be aligned with other international standards, with some respondents directly referencing the Common Vulnerabilities and Exposures system, ISO/IEC 29147 and 30111, and the Computer Misuse Act (1990). A small number of respondents thought that vulnerability disclosure policies should specify that security researchers would not be prosecuted for reporting vulnerabilities.
Some respondents felt that there was a need to specify a timeframe in which “Producers” have to respond to reports of vulnerabilities, as well as that the enforcement authority should be involved in the reporting process.
Q14c Security requirement 3- Provide transparency on for how long, at a minimum, the products will receive security updates
From the 45 responses, a considerable number of respondents agreed with the third security requirement. A broad range of other opinions were expressed in response to this question. Some respondents suggested that the third security requirement should continue to align with existing international standards. Others thought that security updates should be for a minimum period, for example the warranty period or for the life of the product, and that security updates should need to be effective in reaching the owners of in scope devices or in improving security.
Another respondent thought that legislation should require that updates are made available free of charge, and that consumers should be protected from companies adding additional “terms and conditions, privacy policies, or other legal agreements” in order to access security updates.
Other less common responses included requests that “Producers” ensure updates are transparent and intelligible to users, that they share adequate notification of when products will no longer be supported with updates, and that they specify a maximum time frame between notification of a vulnerability and distribution of a security update. However, others felt that the approach should vary depending on the varying difficulties of updates and that it may incentivise manufacturers / “Producers” to shorten their support periods.
Government response (Q14)
We remain confident that the security requirements published in the call for views, and summarised in Key Policy Position 6 strike the right balance of better protecting consumers from online threats and placing acceptable requirements on industry. These security requirements are derived from the top three guidelines of the Code of Practice for Consumer IoT Security, published in 2018.
Given the feedback that our regulations should align closely with internationally agreed technical standards, our intention now is to create an additional route to legal compliance, which would be by means of achieving conformance with designated standards (one of which would be EN 303 645 in the first instance, but this list of designated standards could become longer in the future). This would be an alternative to meeting the security requirements specified in regulation.
Some responses highlighted the importance of product assurance service to achieve good security outcomes. We recognise this and strongly encourage voluntary take-up of assurance services for consumer connected devices. In the future, it may be appropriate to require certain categories of consumer connected devices, especially where the risk to consumers is considered to be high, to undergo an assurance process (for example independent assessment or assisted self-assessment). For that reason, our intended legislation will incorporate powers for Ministers to be able to mandate assurance for designated categories of consumer connected products. We do not have the intention to make use of this power at an initial stage, and would only do so following engagement with industry and analysis of benefits and costs.
Q15a - This proposal requires an exchange of information between “Producers” and “Distributors” in the supply chain to confirm compliance. This places an obligation solely on “Producers” to evidence compliance with the security requirements to the “Distributors”. Should this information exchange approach, as set out in box 6 of the call for views, be adopted?
Summary of responses (Q15a)
| Yes | No, please explain | Don’t know |
|---|---|---|
| 54% | 44% | 2% |
number of yes / no / don’t know responses: 50
Of the 50 responses, a majority agreed that the approach should be adopted.
Within the 22 respondents who indicated that they did not think the proposed approach should be adopted and elected to provide further written feedback, many thought that the “Producer” should provide information, which was the approach the government had proposed. Some others had said that there should be an obligation on both “Producers” and “Distributors”, which was also the approach the government had proposed. A small number of respondents suggested that the information exchange should be aligned with the approach taken for other regulations, and that “Producers” and “Distributors” should go further than a simple information exchange to ensure compliance.
Q15b - Should “Distributors” also have obligations as part of this information exchange?
Summary of responses (Q15b)
| Yes | No, please explain | Don’t know |
|---|---|---|
| 61% | 31% | 8% |
number of yes / no / don’t know responses: 51
While the majority of the 51 responses agreed that “Distributors” should have obligations as part of the proposed information exchange, 16 respondents indicated that they did not agree, and elected to provide further feedback. Some respondents agreed that “Distributors” should have obligations, but with caveats such as that there should be clarity over acceptable methods of due diligence but that “obligations should be minimal and simple”. Some felt that this was not appropriate due to lack of capacity for retailers to check every product that they sell so having to rely on “Producers” to provide accurate information, although the government would like to note that “Distributors” would not be obligated to complete checks for individual units as per the call for views proposals.
Others suggested that the statement of compliance should be standardised, or that “Distributors” should only have to check documents provided by the “Producer”. One respondent thought that the requirements should be consistent with other product legal requirements.
Government response (Q15a + Q15b)
The majority of respondents endorsed the government’s approach. As a result, the government remains confident that the intended approach of placing proportionate obligations on both the manufacturers / “Producers” and “Distributors” of consumer connected products remains the right one. Whilst the intended approach will see manufacturers / “Producers” obligated to provide information on compliance, “Distributors” will also need to play a role, for instance, by verifying that a declaration of conformity has been published. This approach is vital to ensure that the planned legislation is successful in preventing insecure products from being sold to UK consumers, and that consumers have access to important information regarding the security of the products they are able to purchase.
The government has taken on board feedback citing the challenges that could arise from allowing manufacturers / “Producers” to decide how best to provide compliance information to “Distributors”. To this end, the government intends to mandate that manufacturers make a declaration of conformity publicly available for products included within the scope of this regulation. Further details of this are included in Key Policy Position 5.
Q16 - The proposed approach intends to include entities who supply or make smart products available online, e.g. those who act as a marketplace, a platform for consumer sales online or provide either first or third party sales. Do you agree or disagree with this approach?
Summary of responses (Q16)
| Yes | No, please explain | Don’t know |
|---|---|---|
| 83% | 12% | 5% |
Number of yes / no / don’t know responses: 42
Of a total of 42 responses, 35 respondents selected “agree” and elected to provide further written feedback. Several respondents failed to recognise that the government’s proposal is for “distributors” using online marketplaces to be required to comply with the security requirements of the regulation. Others thought that by omitting online marketplaces, there was a risk that this could create loopholes which could be exploited by “Producers”, although the government would like to point out that many of the potential loopholes cited by respondents, such as a mechanism for capturing products manufactured outside of the UK, have been addressed in the government’s proposed approach.
Less common themes identified by a small number of respondents also included that a significant proportion of sales occur via online marketplaces, and that these organisations naturally fall into the proposed definition of “Distributor”, although the government would like to clarify that online marketplaces that undertake activities that would fall within the proposed definition of “Distributor” would be required to adhere to obligations placed on “Distributors” for those activities in the intended legislative approach.
The 5 respondents that selected “disagree” and elected to provide further written feedback each offered differing opinions. It was argued that the seller will be regarded as the “Distributor” and have liability for ensuring standards are met, rendering it unnecessary to place duplicate burdens on marketplaces. It was also claimed that marketplaces cannot carry out due diligence checks if they don’t always have access to the product. Other respondents indicated that it could disadvantage smaller online marketplaces that don’t have the capacity to verify products sold by individuals and that the requirements placed on platforms should not be overly burdensome.
Government response (Q16)
The proposed new security requirements will apply to all consumer products, however they are sold into the UK market. Online marketplaces have brought many benefits to consumers, increasing access to wider ranges of products, innovative products and competitive prices. Online marketplaces have also proven valuable to SMEs and other traders to reach new markets, especially during the Covid-19 pandemic when there have been restrictions on access to non-essential retail stores. Online marketplaces sell the full range of consumer products, not just consumer connected technology. All consumer products, including those sold on online marketplaces, must comply with existing product safety legislation that sets out safety requirements, and that sellers have obligations as “Distributors”. All connected consumer products, sold on online marketplaces or otherwise, will also have to comply with the minimum security baseline set out in this new legislation.
The government is reviewing the UK Product Safety framework to ensure it is fit for purpose, protects consumers and enables business to innovate and grow. The review will consider the impact on product safety of new technologies and new business models. E-commerce will be considered as part of this review. The government will ensure that the approach taken to regulating the security of online products works with the broader approach to product safety adopted once the impact of these business models on safety have been appropriately reviewed.
Q17 - Should the definitions such as “Producer” and “Distributor” (see boxes 5 and 7 in the call for views) in existing product safety regulations (such as the Radio Equipment Regulations 2017, and the General Product Safety Regulations 2005) be used as a basis for the definitions in this proposal?
Summary of responses (Q17)
| Yes | No, please provide details of any alternative approaches that could be considered | Don’t know |
|---|---|---|
| 69% | 23% | 8% |
Number of Yes / No / Don’t Know responses: 52
While the vast majority of the total 52 respondents agreed that the proposed definitions should be used, 12 did not agree and elected to provide further written feedback. Some respondents thought that the definitions should be consistent with existing regulatory definitions. Further feedback included concerns that the “Producer” definition didn’t include software providers and that importers would also be included, who may not be able to fulfil “ongoing obligations that a “Producer” has in respect of management of vulnerabilities and provision of security updates”. One respondent thought that the responsibility of the “Producer” for manufacturing the product and also providing security updates needed to be clearer.
There were mixed views around the definition for “Distributor” with some concerns that it may be difficult to regulate online marketplaces, and that the definition should capture different models for how these organisations operate.
Government response (Q17)
The government appreciates the feedback that respondents provided on the proposed working definitions of relevant economic actors, such as manufacturers / “Producers” and “Distributors”, and has incorporated the views of respondents into the policy development process. We are committed to minimising unnecessary burden on industry, and have been working across government to ensure that the definitions used in our intended legislation align with those used in current and planned future legislation, such as those derived from the New Legislative Framework, where conducive to our objectives.
It should be noted however, that the final legal implementation of the proposed legislation, including the most appropriate definitions of economic actors, would ultimately be determined as part of the legislative drafting process.
Q18a - Box 10 in the call for views describes a suite of example corrective measures and sanctions which could be made available to the enforcement body in the event of non-compliance. Is the proposed suite of corrective measures and sanctions proportionate overall?
Summary of responses (Q18a)
| Yes | No, please explain | Don’t know |
|---|---|---|
| 54% | 41% | 5% |
Number of yes / no / don’t know responses: 56
While the majority of respondents agreed that the proposed suite of corrective measures and sanctions were proportionate overall, 23 respondents did not agree and elected to provide further written feedback. Of these respondents who disagreed, a number of respondents considered a financial penalty of 4% of global turnover to be excessive and that a proportionate approach should be used (although the government would like to clarify that it was not explicitly proposing such a fine in the call for views). One respondent thought that enforcement provisions should follow those in the Health and Safety at Work Act 1974. Others thought that enforcement from other regulations (such as GDPR/ DPA 2018) should also be taken into account when action is taken.
Q18b - Are each of the potential measures below an effective response or deterrent to non-compliance? If no, please explain
Summary of responses (Q18b)
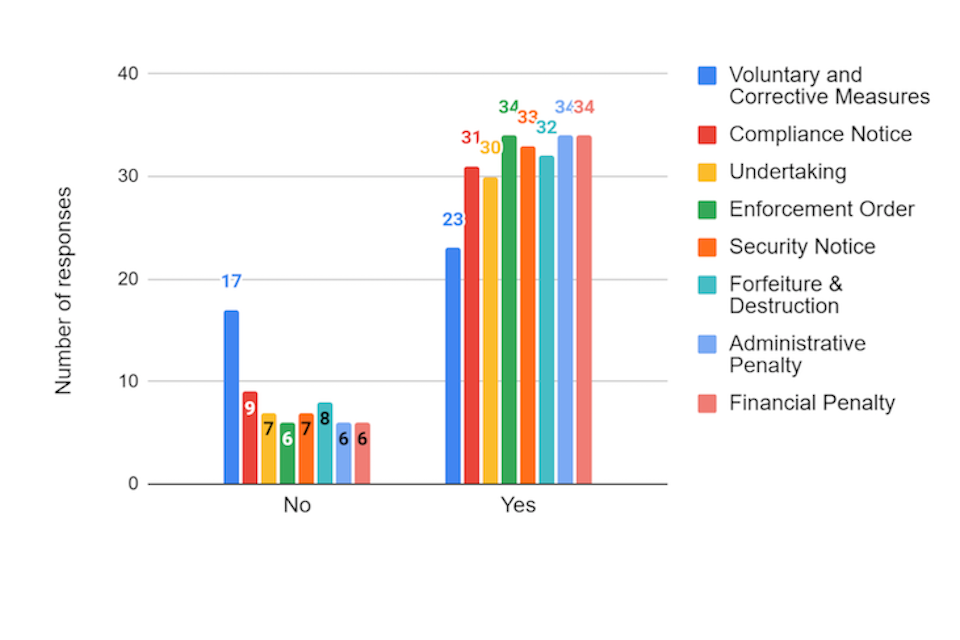
Summary of responses to question 18(b)
| Proposed measure | Number of responses | % of respondents answer yes/no | Number of “no, please explain” qualitative responses | Summary of written feedback (for respondents who selected “no” only |
|---|---|---|---|---|
| Voluntary and Corrective measures | 40 | 57.5% yes 42.5% no | 17 | Many respondents thought that this would be insufficient alone, with some reporting that they thought this didn’t provide an incentive to invest in security. |
| Compliance Notice | 40 | 77.5% yes 22.5% no | 8 | There were a range of views in response to this question. Responses included that penalties should be associated with non-compliance, as well as mandatory timescales to comply. One respondent suggested that this could be included within the voluntary and corrective measures. |
| Undertaking | 37 | 81.1% yes 19.9% no | 6 | One respondent thought that this could be covered by voluntary and corrective measures, while one responded suggested that this option might be more effective against larger companies. Another said that products shouldn’t be sold until the issue was fixed. |
| Enforcement Order | 40 | 85% yes 15% no |
8 | There were a wide variety of responses to this question. Concerns included that enforcement orders should be accompanied by effective sanctions, mandatory timescales should be attached, it should depend on the device or only if the device is unsafe, it may not be as effective for large international companies, that it would take too long and that it should be enforced by an enforcement authority. |
| Security Notice | 40 | 82.5% yes 17.5% no | 6 | A small number of respondents thought that these measures would not be sufficient, with a further stating that it would only be effective if imports were able to be checked continuously. One respondent said that it depended on the device, while another thought that this was appropriate with the possibility to attach civil actions. |
| Forfeiture & Destruction | 40 | 80% yes 20% no | 9 | Some respondents felt that this measure was too strong. One organisation highlighted that destruction may not be necessary if the issue is related to software. An individual suggested that this may not be effective, as businesses may not hold much stock and it may lead to organisations holding more stock overseas in order to minimise the impact of no longer being able to sell to the UK market. |
| Administrative Penalty | 40 | 85% yes 15% no |
7 | Some respondents to this question felt that this measure should be administered by the courts. A small number of others thought that this was not a deterrent. |
| Financial Penalty | 40 | 85% yes 15% no |
8 | The view of many respondents was that any financial penalty needs to be proportionate. Some felt that 4% of annual worldwide turnover was disproportionate, and it has been suggested that it could be based on UK turnover or proportionate to the level of non-compliance. |
Government response (Q18a + Q18b)
The government appreciates the feedback provided by respondents on the effectiveness of the proposed suite of measures. Our intended approach will ensure that the appointed enforcement authority has access to the tools, including notices and civil sanctions, that it needs to manage non-compliance across a range of circumstances, and we will work together with the appointed enforcement authority to ensure that more stringent measures are only deployed when voluntary measures have failed to achieve compliance, or when necessitated by the seriousness of an infraction.
Q19a - Are there significant barriers that would prevent your organisation from becoming compliant with the security requirements within the suggested timescales (see box 9 of the call for views)?
Summary of responses (Q19a)
| Security Requirement | Yes | No | Don’t know |
|---|---|---|---|
| SR1 - No universal default passwords | 39% | 45% | 15% |
| SR2 - Vulnerability disclosure policy | 32% | 50% | 18% |
| SR3 - State minimum update support period | 46% | 40% | 14% |
Number of yes / no / don’t know responses for Security Requirement 1: 33
Number of yes / no / don’t know responses for Security Requirement 2: 34
Number of yes / no / don’t know responses for Security Requirement 3: 35
19b - If there are significant barriers that would prevent your organisation from becoming complaint with the security requirements within the suggested timescales:
-
What are the barriers for implementation?
-
How much time would be required for your organisation to become compliant with the security requirements (in months)
-
How could these barriers be mitigated?
Summary of responses (Q19b)
Security Requirement 1 - Ban universal default passwords
| Feedback requested | Number of qualitative responses | Summary of written feedback |
|---|---|---|
| Barriers for implementation | 15 | Common barriers reported were that this would require a shift in the product development process. Several respondents said that as changes would have to be implemented at the design stage, there would be existing non-compliant stock in warehouses or on the market. Some others thought that there was not enough time to redesign products. |
| How long would it take to become compliant (months) | 12 | Several respondents thought that compliance would take over 18 months, with 24 months a common response. Some responded 7-12 months, which was the minimum reported. |
| How barriers could be mitigated | 10 | Some respondents thought that the obligations should only apply to products placed on the market after a specific date and that existing products should be exempt. One requested further clarity on how the cut off date would be determined, whether it would be from the date of manufacturing or sale. One suggested that devices should not be functional until a consumer has entered new credentials, while another suggested a single timescale for all requirements. One respondent also requested that there were exemptions for research provided that a formal risk assessment is documented and outcomes explained to all those involved. |
Security Requirement 2 - Implement means to manage reports of vulnerabilities
| Feedback requested | Number of qualitative responses | Summary of written feedback |
|---|---|---|
| Barriers for implementation | 12 | A lack of resources was reported as a barrier by some respondents, with some others requesting more clarity around obligations and scope of the requirement. Others also mentioned challenges around implementing and managing internal processes for vulnerability disclosure. |
| How long would it take to become compliant (months) | 11 | There were a range of timescales reported for this question. 7-12 months was most commonly reported by respondents, followed by a small number of responses of 13-18 months and over 18 months. One respondent also answered for each option 1-3 months and 4-6 months, with one respondent already having a process in place. |
| How barriers could be mitigated | 7 | Some respondents suggested that there should be a grace period for legacy products that are already on the market. Another suggested that there could be online reporting via a webform. |
Security Requirement 3 - Transparency on minimum time products will receive security updates
| Feedback requested | Number of qualitative responses | Summary of written feedback |
|---|---|---|
| Barriers for implementation | 16 | Several respondents felt that there was ambiguity in aspects of this requirement, including whether this would be required to be stated on the product/ manuals, the point at which the minimum time is measured from, and whether third party and software update agreements are included in scope. |
| How long would it take to become compliant (months) | 12 | Over 18 months was the most common answer to this question, followed by 7-12 months. A further one respondent reported immediately, and one reported 1-3 months. A small number of respondents highlighted that this could, however, depend on the product or the operating system. Other barriers reported included having to modify contracts with suppliers and having to establish support periods for every hardware and software component in a device, both of which require time. |
| How barriers could be mitigated | 9 | Several respondents thought that barriers could be mitigated by having a grace period, exemptions or special arrangements for existing products on the market. Other views, reported by one respondent each, included that this requirement should be aligned with the warranty period; that it should be implemented once the UK has a working relationship with the EU settled and recovered from COVID-19; and that an end-of-life policy should be used rather than a specified period for updates. |
Government response (Q19a + 19b)
The government appreciates the complexities that some organisations will face in implementing the initial set of security requirements it is seeking to mandate. Whilst the government is seeking to introduce legislation in this space when parliamentary time allows, and we remain committed to ensuring that businesses are given an appropriate amount of time to adjust their business practices before instances of non-compliance are actively enforced.
In light of the impending regulation, we would urge manufacturers that have not already done so to take steps to implement cyber security measures in line with our intended security requirements, using available guidance, such as that produced by the Internet of Things Security Foundation (IoTSF) and Oxford Information Labs (OXIL), as necessary.
Q20 - Please provide details of any additional costs to your organisation that would result from implementing each of the security requirements in our proposed approach. Please also provide details of any benefits to your organisation that would result from the implementation of these security requirements.
Summary of responses (Q20)
Security Requirement 1 - Ban universal default passwords
| Information requested | Number of qualitative responses | Summary of written feedback |
|---|---|---|
| Description of additional costs | 14 | Whilst some respondents cited no additional costs resulting from implementing the security requirements, other respondents anticipated increased costs resulting from a number of areas, including the need to conduct additional product testing, for additional supply chain reviews, bringing together and maintaining complex datasets, or the redrafting of contracts. |
| Job roles involved and number of hours required per job role | 7 | Respondents cited the involvement of engineers, developers, product compliance managers, and security experts, amongst others. |
| Estimated total cost per product line (£) | 5 | Some respondents indicated that it was too soon to determine the cost of implementing this requirement per product line. Monetary answers provided ranged from £400 to £100,000, though this range should be interpreted with caution, as respondents provided varying degrees of context to any monetary answers provided. |
| Estimated total annual cost to your organisation (£) | 7 | Some respondents indicated that it was either too soon or too difficult to determine the total annual cost of implementing this requirement. Monetary answers provided ranged from £70,000 to £145,000, though this range should be interpreted with caution, as respondents provided varying degrees of context to any monetary answers provided. |
| Details of benefits to your organisation that would result from implementation | 22 | Many respondents cited increased resistance to cyber attacks and generally improved security as key benefits for their organisations as a result of implementation. Other respondents noted increased consumer confidence as a key benefit, and one respondent added that implementation would improve trust and transparency in the industry as a whole. Of the respondents that saw no benefits to their organisation, several noted that this was because their organisation was already compliant with existing guidelines, thus limiting the potential for additional benefit as a result of implementation |
Security Requirement 2 - Implement means to manage reports of vulnerabilities
| Information requested | Number of qualitative responses | Summary of written feedback |
|---|---|---|
| Description of additional costs | 10 | Although some respondents cited the additional costs required to establish or maintain a vulnerability management system, overall, the response rate for this question was prohibitively low for any other themes to be identified. |
| Job roles involved and number of hours required per job role | 7 | Not enough of the information and the varying degrees of context provided in response to this question was relevant enough for any themes to be identified. |
| Estimated total cost per product line (£) | 2 | Because of the lack of information and the varying degrees of context provided in response to this question, it would not be appropriate to determine any themes from the feedback provided. |
| Estimated total annual cost to your organisation (£) | 6 | Some respondents indicated that it was either too soon or too difficult to determine the total annual cost of implementing this requirement. Monetary answers provided ranged from £10,000 to £80,000, though this range should be interpreted with caution, as respondents provided varying degrees of context to any monetary answers provided. |
| Details of benefits to your organisation that would result from implementation | 19 | Several respondents suggested that improving the security of future products and revealing emerging vulnerabilities would benefit their organisation. One respondent noted that reducing the chance of a vulnerability going unreported due to administrative errors was an additional benefit. A number of other respondents felt that the benefits to their organisation would be limited or nil, with a small number noting that their organisation’s compliance with existing guidelines limits the additional benefits that can be gained by implementation. |
Security Requirement 3 - Transparency on minimum time products will receive security updates
| Information requested | Number of qualitative responses | Summary of written feedback |
|---|---|---|
| Description of additional costs | 11 | Some respondents cited additional costs related to setting up new systems or changing information flows to enable this requirement to be met. Some respondents misinterpreted the requirement to be an obligation to provide security updates, as opposed to providing transparency on how long products will receive security updates for. Overall, the response rate was prohibitively low for further trends to be identified. |
| Job roles involved and number of hours required per job role | 7 | A range of job roles involved were cited by respondents as relevant, including factory staff; developers; artwork staff; website admin staff; testers; sales/marketing administrators and software development staff. The hours required per job role ranged from 1-2 weeks for development and testing staff, to 2-3 hours for factory staff and artwork staff respectively. |
| Estimated total cost per product line (£) | 4 | Because of the lack of information and the varying degrees of context provided in response to this question, it would not be appropriate to determine any themes from the feedback provided. |
| Estimated total annual cost to your organisation (£) | 4 | Because of the lack of information and the varying degrees of context provided in response to this question, it would not be appropriate to determine any themes from the feedback provided. |
| Details of benefits to your organisation that would result from implementation | 19 | Many respondents referenced increased consumer confidence in their products as a key benefit, while others cited an improved reputation of their organisation amongst consumers. A small number of respondents added that their customers would benefit from easier products differentiation as a result of implementation. Of the respondents that indicated no benefits to their organisation would result from implementation, the majority reasoned that their existing adherence to security update guidelines limited the potential benefits for their organisation. |
Government response (Q20)
Whilst the low response rate for this question has precluded us from being able to generate representative insights for use in our final stage regulatory impact assessment, the responses have been considered as part of our wider policy development and impact assessment work, and the government is grateful to the organisations that took the time to provide detailed information on the impact that implementing the security requirements could have on their businesses.
The government will publish a regulatory impact assessment detailing its assessment of the material costs and benefits of the intended legislation before it comes into force.
Q21a - Please estimate any additional reporting impacts or costs to your organisation resulting from:
- The proposed obligation for “Producers” to demonstrate compliance with the security requirements to “Distributors”
- The requirement for “Distributors” to process information from “Producers”
Summary of responses (Q21a)
The proposed obligation for “Producers” to demonstrate compliance with the security requirements to “Distributors”
| Information requested | Number of qualitative responses | Summary of written feedback |
|---|---|---|
| Description of costs | 4 | Because of the lack of information and the varying degrees of context provided in response to this question, it would not be appropriate to determine any themes from the feedback provided. |
| Job roles involved and number of hours required per job role | 2 | Too little information was provided for any themes to be identified. |
| Estimated total cost per product line (£) | 2 | Too little information was provided for any themes to be identified. |
| Estimated total annual cost (£) | 2 | Too little information was provided for any themes to be identified. |
The requirement for “Distributors” to process information from “Producers”
| Information requested | Number of qualitative responses | Summary of written feedback |
|---|---|---|
| Description of costs | 2 | Too little information was provided for any themes to be identified. |
| Job roles involved and number of hours required per job role | 1 | Too little information was provided for any themes to be identified. |
| Estimated total cost per product line (£) | 1 | Too little information was provided for any themes to be identified. |
| Estimated total annual cost (£) | 1 | Too little information was provided for any themes to be identified. |
Q21b - Are there any ways we could tailor our approach to mitigate these reporting impacts?
Summary of responses (Q21b)
| Yes, please explain | No | Don’t know |
|---|---|---|
| 63% | 5% | 32% |
Number of yes / no / don’t know responses: 19
Of the 11 respondents that indicated that the government’s proposed approach could be tailored to mitigate reporting impacts, and elected to provide further written feedback, a number of views were expressed. These views ranged from highlighting that international cooperation and alignment would be vital for the success of the wider approach, to views that the obligation for “Producers” to prove compliance to “Distributors” was unnecessary.
Government response (Q21a + Q21b)
Whilst the low response rate for this question has precluded us from being able to generate representative insights for use in our final stage regulatory impact assessment, the responses have been considered as part of our wider policy development and impact assessment work. The government is grateful to the organisations that took the time to provide detailed information on the impact that the proposed reporting obligations would have on their businesses.
The government will publish a regulatory impact assessment detailing its assessment of the material costs and benefits of the intended legislation before it comes into force
Q22a - To what extent do you agree or disagree with the criteria that would be considered for identifying an enforcement body, detailed in box 12 of the call for views?
Q22a -Summary of responses
| Strongly disagree | Somewhat disagree | Neither agree/disagree | Somewhat agree | Strongly agree |
|---|---|---|---|---|
| 2% | 2% | 17% | 41% | 37% |
Number of likert scale responses: 46
6.1 Q22b - To what extent do you agree or disagree with the example powers for the enforcement body, detailed in box 13 of the call for views document?
Q22b - Summary of responses
| Strongly disagree | Somewhat disagree | Neither agree/disagree | Somewhat agree | Strongly agree |
|---|---|---|---|---|
| 0% | 9% | 22% | 24% | 44% |
Number of likert scale responses: 45
Government response (Q22a + Q22b)
The government is appreciative of the supportive feedback for the example considerations for designating an enforcement authority included in the call for views. These considerations have been incorporated into the design of the methodology employed by officials to appoint the most appropriate enforcement authority for the intended legislation. This process is still ongoing, and the government will announce the identity of the intended enforcement authority in due course.
It is vital that our intended legislation provides the selected enforcement authority with appropriate powers so that it can respond in a proportionate manner across a range of contexts to eliminate non-compliance, and we will continue to work across government to ensure that the appointed enforcement authority is equipped with the tools it needs to manage non-compliance.
-
EN standards are set by ETSI, which is a standards development organisation that develops globally-applicable standards, with members drawn from 65 countries. ETSI is a globally-applicable standards development organisation (SDO) with members drawn from 65 countries. EN 303 645 is the world’s premiere consumer internet of things security standard, with global uptake. ↩
